
Artech Information Systems, one of the largest US IT staffing companies, has disclosed a data breach caused by a ransomware attack that affected some of its systems during early January 2020.
Artech is a privately-held firm with an estimated $810 million annual revenue run rate for 2019 and more than 10,500 employees and consultants across the 40 US states, Canada, India, and China.
The company provides staffing and workforce solutions, program management, and government services, and its customer list includes over 80 Fortune 500 clients and US federal government entities.
Ransomware deployed three days after initial breach
The ransomware attack was discovered by Artech after finding ransomware on some systems following reports of unusual activity related to one of its employee’s user accounts.
"That same day Artech engaged a leading third-party forensic investigation firm to assess the security of its systems and to confirm the nature and scope of the incident," a data breach notification letter sent to affected individuals explains [1, 2].
"On January 15, 2020, the investigation determined that an unauthorized actor had access to certain Artech systems between January 5, 2020, and January 8, 2020."
BleepingComputer learned of the attack on Artech's servers on January 11, 2020, when the REvil (Sodinokibi) ransomware gang leaked 337MB of what they claimed to be stolen files from the company's servers.
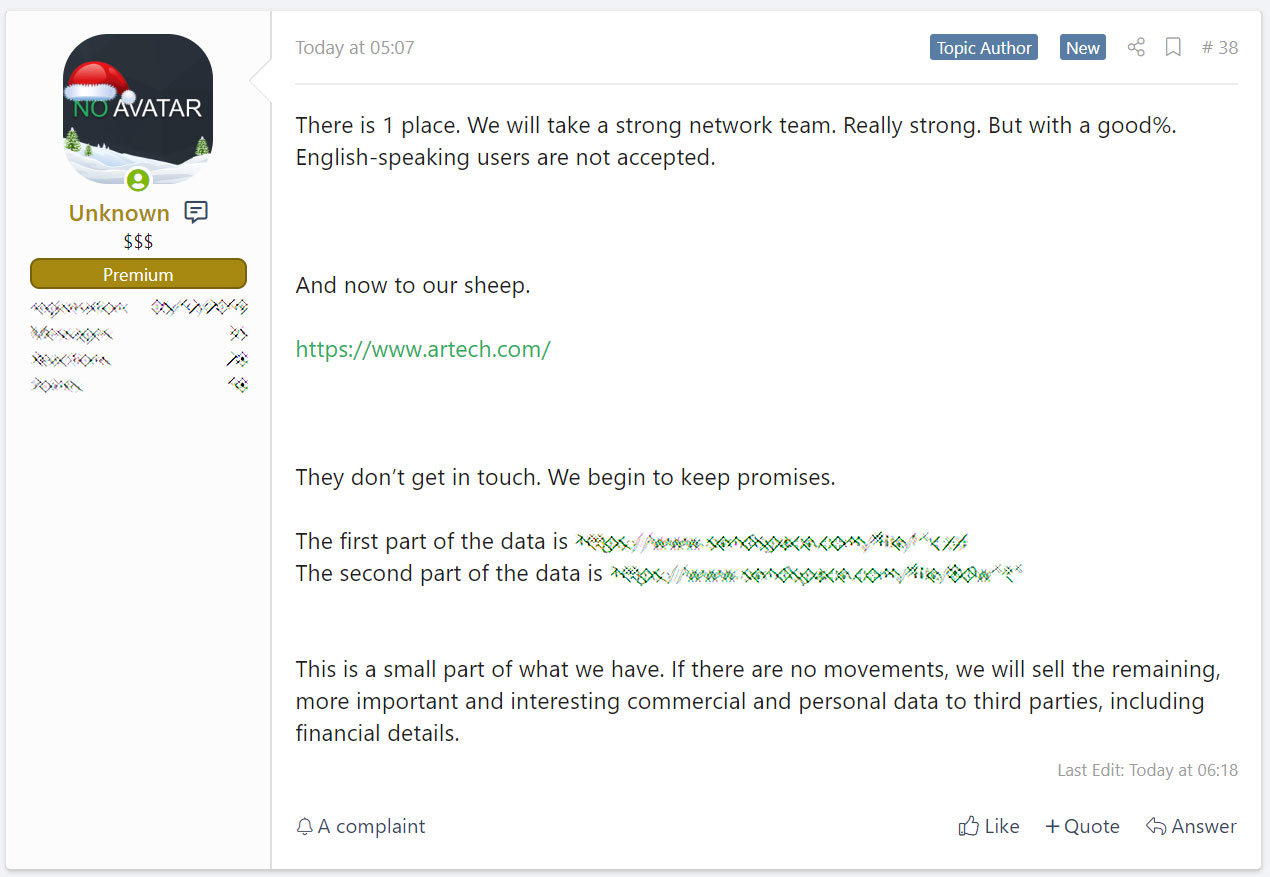
"This is a small part of what we have," REvil's operators said at the time. "If there are no movements, we will sell the remaining, more important and interesting commercial and personal data to third parties, including financial details."
BleepingComputer reached out to Artech to find if they were aware of the attack and the ransomware group's claims but our emails were ignored, with no answer received until we published this article.
However, an email shared with BleepingComputer by an Artech employee stated that the company had to shut down all systems, but were able to restore critical services and servers from backup data.
CVE-2019-11510 strikes again. Their Pulse Secure VPN (https://t.co/cNrZ4GjwEQ) server went unpatched for months and months.
— Bad Packets (@bad_packets) September 11, 2020
REvil is a ransomware-as-a-service (RaaS) operation that breaches corporate networks via exposed remote desktop services and compromised Managed Service Providers, as well as by using exploits and spam emails.
Once they gain access to a victim's network, the REvil operators will spread laterally stealing sensitive data to be used as leverage to pressure the victims into paying the ransom under the threat of publicly leaking the info.
After gaining administrative access to a domain controller and stealing data from servers and workstations, REvil deploys ransomware payloads on all computers on the company's compromised network.
Personal, financial, and health info exposed in the attack
While investigating the incident, Artech discovered personal, health, and financial information of multiple individuals stored on the compromised systems.
Around June 25, 2020, when the company completed the attack investigation, it was able to determine the individuals who had their information impacted during the ransomware attack.
"The investigation determined that at the time of the incident the involved files may have contained information including name, Social Security number, medical information, health insurance information, financial information, payment card information, driver’s license/state identification number, government-issued identification number, passport number, visa number, electronic/digital signature, username and password information," Artech says.
The combination of exposed information is different for every affected individual according to the company's breach notification letter.
After discovering the attack Artech changed systems credentials to secure its systems and started working with external security experts to improve the company's existing security processes and protocols.
Artech urges affected individuals who received the data breach notice to monitor their account statements for suspicious activity and to be vigilant against fraud and identity theft attempts. The company also provides them with free credit monitoring and identity protection services through Kroll.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now