A ransomware strain known as Scarab, and detected for the first time in June, is now being pushed to millions of users via Necurs, the Internet's largest email spam botnet.
The spam campaign started in the early hours of the morning (EU timezones) and has been spotted by all security researchers not busy celebrating Thanksgiving. This includes reports from F-Secure, Forcepoint, MalwareHunter, and MyOnlineSecurity.
Necurs pushed tens of millions of spam emails carrying Scarab
According to Forcepoint, by noon, Necurs had already sent out 12.5 million emails carrying what appeared to be a new version of the Scarab ransomware.
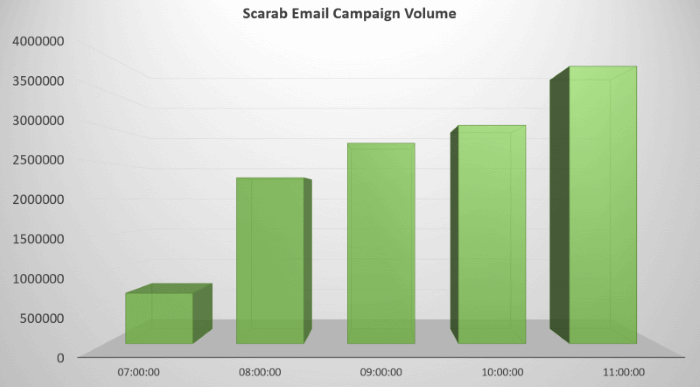
The impact of this increased activity was immediately picked up on ID-Ransomware, a service that allows users to detect the type of ransomware that infected their system, where Scarab detections started going up.
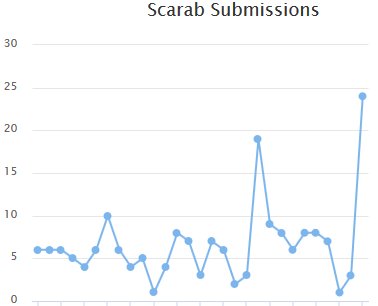
Scarab is the fourth ransomware strain Necurs has pushed this year, after Locky, Jaff, and GlobeImposter. The botnet also pushed the Dridex banking trojan —it's typical payload—, the Trickbot banking trojan, and pump-and-dump schemes.
All of the three abovementioned ransomware strains have been a problem for users this year. If its partnership with Necurs continues in the coming weeks, Scarab is about to give users and researchers alike a lot of headaches.
Scarab emails disguised as archives carrying scanned images
The emails delivering the Scarab ransomware followed a pattern seen in the past with Necurs spam. The email subjects gave the illusion the attached documents were images of scanned documents. The most popular subject lines seen today were:
Scanned from HP
Scanned from Canon
Scanned from Epson
These emails carried a 7Zip archive that contained a Visual Basic script. The script would download and run an EXE file —the Scarab ransomware.
This Visual Basic script contained the same Game of Thrones references that were seen in September in Necurs campaigns that pushed the Locky ransomware.
The Scarab ransomware
The Scarab ransomware is a relatively new ransomware strain that was first spotted by security researcher Michael Gillespie in June this year.
Written in Delphi, the first version was simplistic and was recognizable via the ".scarab" extension it appended after the names of encrypted files.
Malwarebytes researcher Marcelo Rivera spotted a second version in July that used the ".scorpio" extension. The version spotted with the Necurs spam today has reverted back to using the .scarab extension.
The current version of Scarab encrypts files but does not change original file names as previous versions. This Scarab version appends each file's name with the ".[suupport@protonmail.com].scarab" extension.
Scarab also deletes shadow volume copies and drops a ransom note named "IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT" on users' computers, which it opens immediately.
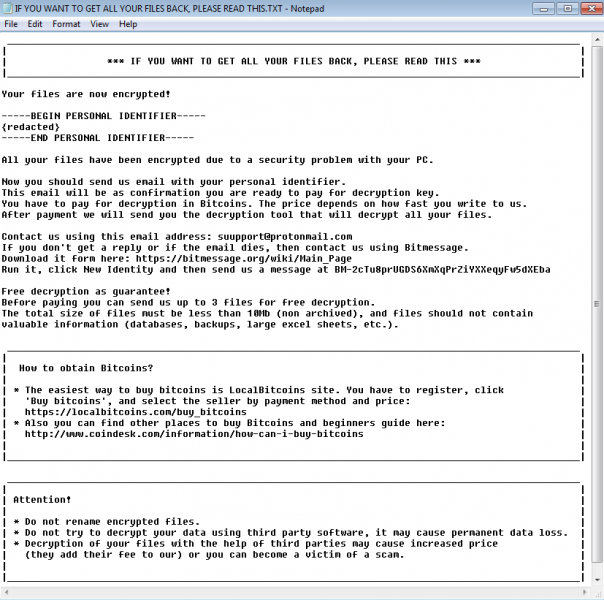
The ransom note is peculiar because it does not mention a ransom sum, but tells users that the quicker they contact the Scarab authors via email or BitMessage, the smaller the ransom sum will be.
At the time of writing, there is no known method of recovering files encrypted by the Scarab ransomware. It also doesn't appear that Scarab is the work of the Necurs botnet maintainers, and more likely that this is only another ransomware crook renting the botnet's spam cannon, similar to GlobeImposter campaigns.
A first version of this article incorrectly stated that Scarab was based on the Hidden Tear open source ransomware building kit.
Image credits: Laymik, Forcepoint, Bleeping Computer, MalwareHunter


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now