
Chinese Volt Typhoon state hackers failed to revive a botnet recently taken down by the FBI, which was previously used in attacks targeting critical infrastructure across the United States.
Before KV-botnet's takedown, it allowed the Volt Typhoon threat group (aka Bronze Silhouette) to proxy malicious activity through hundreds of compromised small office/home offices (SOHO) across the U.S. to evade detection.
However, after obtaining a court order authorizing it to dismantle the botnet on December 6, FBI agents took control of one of its command-and-control (C2) servers and cut off the Chinese hackers' access to the infected devices (i.e., end-of-life Netgear ProSAFE, Cisco RV320s, and DrayTek Vigor routers, and Axis IP cameras).
Two days later, Volt Typhoon started scanning the Internet for more vulnerable devices to hijack and rebuild the dismantled botnet.
According to a report from Lumen Technologies' Black Lotus Labs team, the threat actors carried out a large-scale attack on 3,045 devices, including a third of all the NetGear ProSAFE routers exposed online globally. Out of these attempts, they managed to infect 630 devices
"We observed a brief but concentrated period of exploitation activity in early December 2023, as the threat actors attempted to re-establish their command and control (C2) structure and return the botnet to working order," Lumen Technologies' Black Lotus Labs team said.
"Over a three-day period from December 8 to December 11, 2023, KV-botnet operators targeted approximately 33% of the NetGear ProSAFE devices on the Internet for re-exploitation, a total of 2,100 distinct devices."
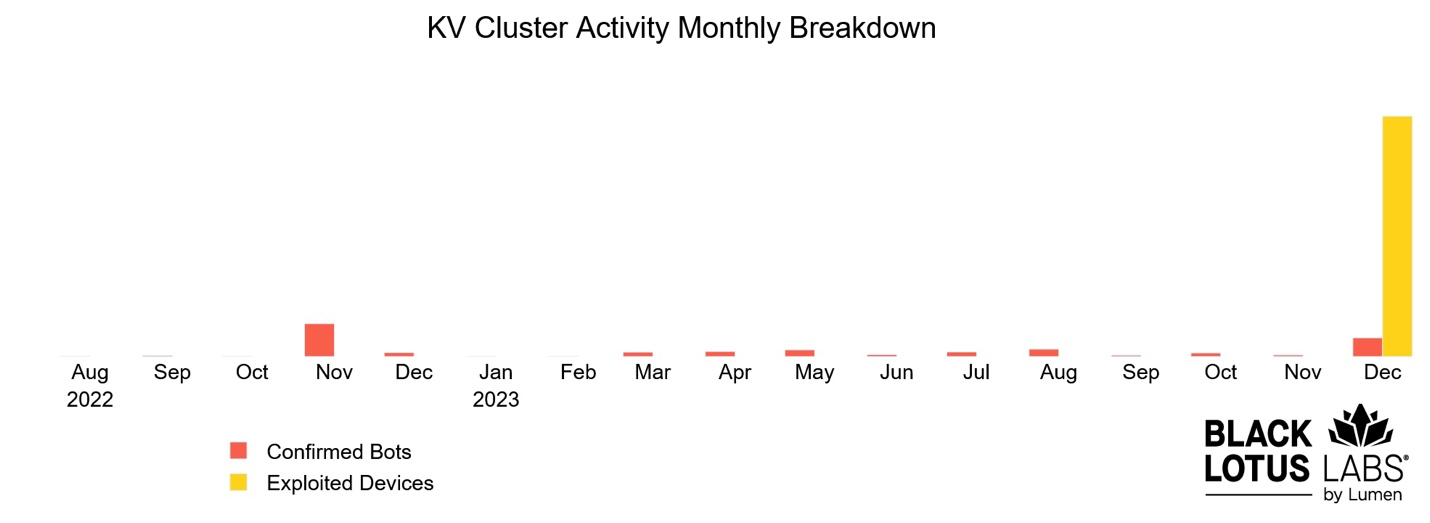
However, despite their concerted efforts, Black Lotus Labs thwarted the Chinese hackers' attempts to revive the botnet by null-routing the attacker's entire C2 and payload server fleet over a month, between December 12 and January 12.
Since the last KV-botnet beacon was observed on January 3, no other C2 servers have been activated.
"The lack of an active C2 server combined with the FBI court-authorized action against KV-botnet and Lumen Technologies persistent null-routing of current and new KV cluster infrastructure provides a good indication that the KV activity cluster is no longer effectively active," Black Lotus Labs said.
Volt Typhoon has been breaching U.S. critical infrastructure since at least mid-2021, using a KV-botnet cluster of compromised Fortinet FortiGate firewalls (active until August 2023) as a springboard for their attacks.
The list of organizations the Chinese cyber spies have breached and targeted includes U.S. military organizations, telecommunication and internet service providers, as well as a European renewable energy firm.
One week ago, CISA and the FBI urged SOHO router manufacturers to ensure their devices are secure against Volt Typhoon's ongoing attacks by using secure configuration defaults and eliminating web management interface flaws during development.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now