
Hosting provider Hostinger today announced that it reset the login passwords of 14 million of its customers following a recent security breach that enabled unauthorized access to a client database.
The incident occurred on August 23 and a third party was able to access usernames, hashed passwords, emails, first names, and IP addresses.
Unauthorized server access
Hostinger offered more details about the incident in a blog post today, saying that an unauthorized party accessed one of their servers and was then able to obtain further access to customer information.
This was possible because the server had an authorization token that allowed access and privilege escalation to a RESTful API used for queries about customers and their accounts, including phone numbers and home address or business address.
"The API database, which includes our Client usernames, emails, hashed passwords, first names and IP addresses have been accessed by an unauthorized third party. The respective database table that holds client data, has information about 14 million Hostinger users."
The password reset action is a precautionary measure and Hostinger clients received the notification and details on how to regain access to their account.
Financial data and websites have not been impacted in any way, the company says. Payment for Hostinger services is done through a third-party provider and an internal investigation found that data regarding websites, domains, hosted emails "remained untouched and unaffected."
Set unique passwords
Hashing the passwords is a good way to prevent intruders from getting sensitive information in cleartext. However, the passwords of Hostinger clients may still be at risk as the company used the SHA1 algorithm for the scrambling.
One Hostinger customer affected by the incident contacted the company to ask about the hashing algorithm used to scramble the passwords. The reply came that the data was hashed with SHA-1, and now SHA-2 is used for the reset passwords.
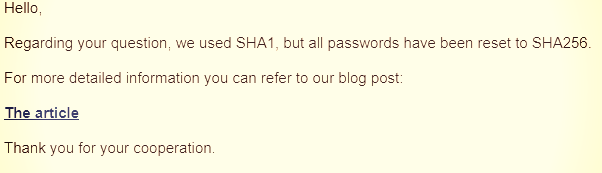
SHA-1 has been in use for a much longer time than SHA-2 and there are extensive databases with billions of hashes and their original input (rainbow tables) that could be used to find out the passwords.
Attackers use passwords obtained this way in credential stuffing attacks, trying them on accounts for various other services and hoping that the victim reused them.
The Secure Hash Algorithm (SHA) functions are fast and allow for quick computation in an offline crack attack. A slower variant, such as bcrypt, is regarded as more suitable for hashing passwords.
Hostinger warns that this incident may be leveraged in phishing campaigns seeking login details, personal information or to direct to malicious websites.
A strong recommendation is to use strong passwords that are unique for each online service. Password managers can both generate and store them securely.
The investigation of this incident is ongoing and a team of internal and external forensic experts are looking into the breach point. Authorities have also been contacted and clients have been informed.
One security feature that Hostinger plans to add in the near future is support for two-factor authentication (2FA). This would ensure that the username and password alone are not enough to gain access to an account.
h/t SickSkillz


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now