
Recent versions of the Carbanak malware are now abusing several Google services to host command-and-control (C&C) infrastructure, which they use to manage infections and exfiltrate stolen data.
Carbanak is the name of a financially-motivated cyber-criminal group that operates with the help of a custom-made malware family, also named Carbanak.
It's stealthy and unique malware allowed the group to work for several years without being detected. Nonetheless, by 2015, security firms had caught up with the crooks' activities, when Kaspersky exposed a campaign during which the Carbanak gang stole over $1 billion from banks across the world.
Ever since then, the group's movements have been closely watched by security researchers. One of the companies that recently came across versions of the Carbanak malware is Forcepoint, who also noticed a significant shift in the group's mode of operation.
Carbanak C&Cs: Google Apps Script, Google Sheets, and Google Forms
According to Forcepoint, the Carbanak malware now uses several Google services to host C&C infrastructure, such as Google Apps Script, Google Sheets, and Google Forms.
Victims are targeted using spam email that contains boobytrapped Word documents. These documents come with embedded OLE objects disguised as images. Users are told to double-click to unlock the document's content, but they are actually installing the Carbanak malware on their PCs.
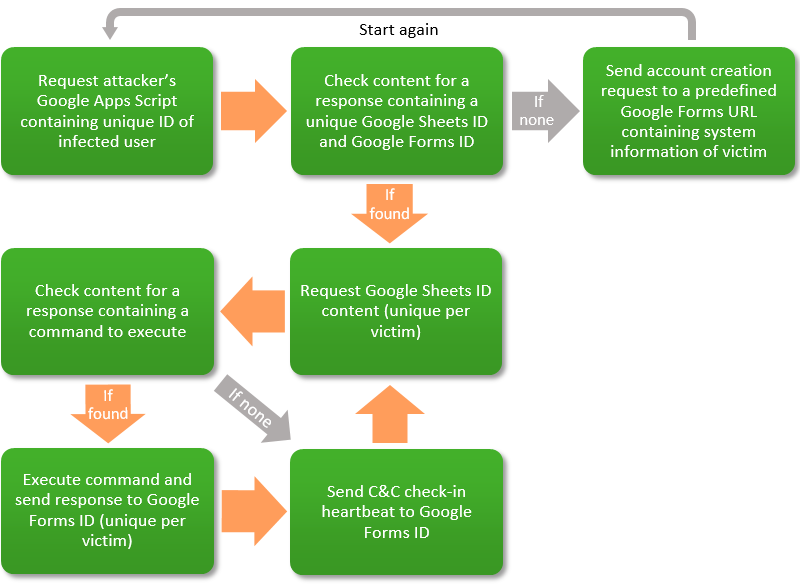
After the infection takes root, the malware generates a unique ID for each infected computer. In previous versions, the Carbanak malware would contact a web server and receive commands to execute, and also upload stolen information to another web or FTP server.
In the version recently discovered by Forcepoint, the malware pings a Google Apps Script with the victim's ID. If the Google Apps Script has an entry for that ID, it will provide the malware with the URLs of a Google Spreadsheet and a Google Forms.
The Google Spreadsheet stores configuration info and commands the malware needs to execute, while the Google Forms URL is used to upload all stolen information.
If the Google Apps Script doesn't hold an entry for a new victim ID, it will create one and pass it on.
Forcepoint says it's working with Google to shut down the Carbanak gang's operations.
Previously, the same gang has been observed by security firm Trustwave, who said the group's members were targeting call center operators at the companies they wanted to hack and tricking them into running malicious files to get an initial foothold on the company's network.
An in-depth overview of recent Carbanak attacks is also available via the Digital Plagiarist report from Tr1adx and the Grand Mars report from Trustwave.
In July 2016, the cuteRansomware family used Google Docs to store information on infected victims.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now