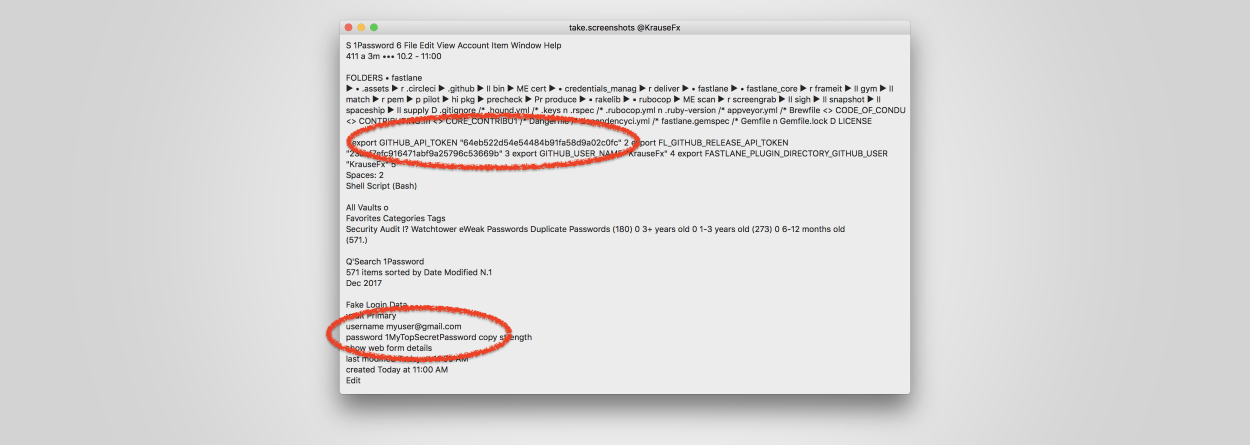
Malicious app developers can secretly abuse a macOS API function to take screenshots of the user's screen and then use OCR (Optical Character Recognition) to programmatically read the text found in the image.
The function is CGWindowListCreateImage, often utilized by Mac apps that take screenshots or live stream a user's desktop.
API function can be abused to read sensitive user data
According to Fastlane Tools founder Felix Krause, any Mac app, sandboxed or not, can access this function and secretly take screenshots of the user's screen.
Krause argues that miscreants can abuse this privacy loophole and utilize CGWindowListCreateImage to take screenshots of the screen without the user's permission.
In experiments he carried out, Krause says he was able to use an OCR library to read various types of information captured using CGWindowListCreateImage. He argues that an attacker can:
⌔ Read sensitive source code, API keys, or similar data
⌔ Read emails and messages users open on their Mac
⌔ Detect what web services users employ (e.g. email providers, password manager, app lists, etc.)
⌔ Learn personal information about the user, like their bank details, salary, address, etc.
In an email conversation with Bleeping Computer, Krause says he privately reported the issue to Apple last November. Because the issue was not resolved, Krause went public with his findings on his blog yesterday, and filed a public bug with Apple.
Researcher proposes possible mitigations
Krause also proposed some mitigations that Apple could take into consideration to prevent abuse of the CGWindowListCreateImage function.
The easiest one to implement would be to put the user in charge by adding a permission dialog for apps that use this function to take screenshots of the user's screen.
Another one would be to have macOS to notify users when an app is taking screenshots of his screen, a notification system that Mac security software can tap into and block such attempts.
"There are lots of valid use-cases for Mac apps to record the screen, e.g. 1Password 2fA support or screen recording software, however there must be some kind of control," Krause said.
This is not the first time Krause has looked at the privacy controls of Apple features. Last year, the researcher discovered that rogue iOS applications can gain access to limited geo-location information by obtaining image permissions and extracting GPS coordinates from locally-stored photos.
Article updated with Krause's email response, clarifying that he privately reported the issue to Apple last November.
.jpg)

Comments
michaelbadichi - 6 years ago
I don't know why you focus on macOS (and on this api in particular and not for example CGDisplayCreateImageForRect), when this can also be achieved on windows (BitBlt/GetDIBits and other), or linux (various ways)...
actually these are the "simple" techniques, there are also techniques for grabbing displays on the GPU level, which is not even aware to the OS isolation abilities (if any).