Some of the most popular Android applications installed on your phone may be vulnerable to a new type of attack named "Man-in-the-Disk" that can grant a third-party app the ability to crash them and/or run malicious code.
Discovered by the Check Point team, the Man-in-the-Disk (MitD) attack scenario revolves around an app's ability to use "External Storage," one of the two types of data storage methods supported by the Android OS.
What's Internal and External Storage?
To better understand the attack, a general knowledge of the Internal and External Storage concepts is necessary.
Internal Storage, also known as System Memory, is a section of an Android's phone's built-in storage space that stores the operating system itself, system apps, drivers, and selected data of user-installed apps.
Each installed app can allocate itself "internal storage" space that is protected by a sandboxed environment, meaning it can't be accessed by any other app.
Some app developers don't like using too much Internal Storage space as it may deter some users from installing apps that take too much space on their phone. Instead, they ask for the permission to access External Storage and store app-specific files there, as they don't count for an app's total "install size."
External Storage is a common storage space, usually made up with what's left of the phone's built-in hard drive and any additional SD cards or USB storage devices connected to the phone.
How the Man-in-the-Disk attack works
The Man-in-the-Disk attack works because of two reasons. First, any app can tamper with another app's External Storage data. Second, because almost all apps ask for this permission, users are generally willing to give it and unaware of any security risks.
During tests, Check Point researchers said they were able to create a malicious app that appeared as a benign flashlight app that asked for the permission to store data on a device's External Storage space, and used this permission to attack other apps.
Researchers say they were able to carry out two types of attacks —to crash other apps and to update other apps to malicious versions.
The first attack works by meddling with another app's External Storage files by inserting malformed data that causes the app to crash. This first type of attack can be used to sabotage a competing app or to trigger a crash that leaves doors open to exploiting other loopholes and inject malicious code inside the crashed app.
If the crashed app has more permissions than the original (flashlight) app, this means the attacker can elevate his permissions and access more sensitive phone features via the crashed app —features for which he would have needed to request permissions, and which he would have certainly not received for the original flashlight app.
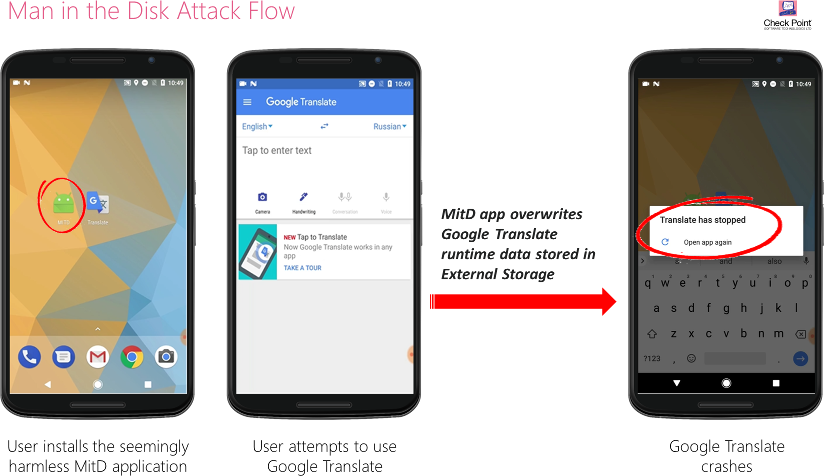
In the second type of MitD attack, Check Point researchers say that an attacking app can monitor the External Storage space for moments when apps are receiving updates.
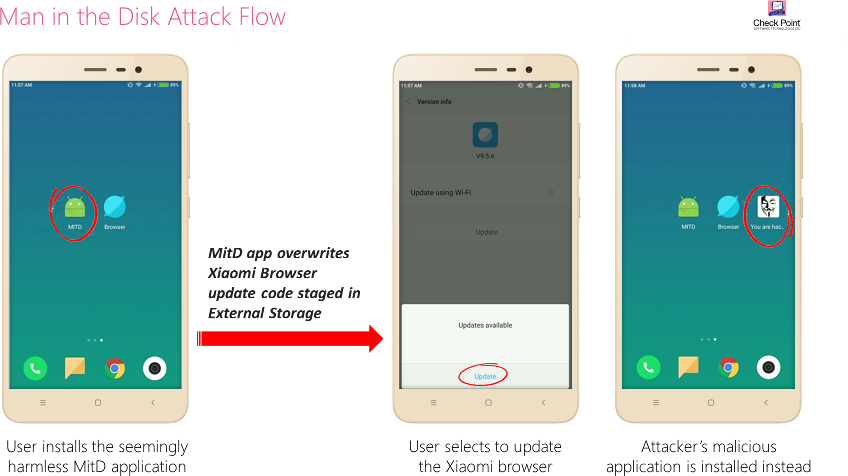
Because some apps use External Storage to store temporary update files before applying the update, researchers say that an attacker can easily replace those files on the External Storage space and trick the app into installing a malicious version of itself, or another malicious third-party app altogether.
Google and Yandex apps vulnerable to MitD
During tests, Check Point says it identified some very popular apps vulnerable to the two versions of MitD attacks, including in some Google apps that come preinstalled on the vast majority of Android devices sold on the market.
For example, Google Translate, Google Voice Typing, Yandex Translate, and Yandex Search were vulnerable to crash-type MitD attack, while the insanely popular Xiaomi Browser was vulnerable to the malicious-update-type MitD attack.
Researchers say they only tested these apps, and are certain that many other apps are also vulnerable to one of the two MitD attacks, if not both.
App developers not following security best practices
According to the research team, the reasons why MitD attacks are possible, to begin with, is because app developers —apparently even those at Google— are not following Android security guidelines that recommend simple measures for working with External Storage.
▻ Perform input validation when handling data from external storage
▻ Do not store executables or class files on External Storage
▻ External Storage files should be signed and cryptographically verified prior to dynamic loading
Check Point recommends that app developers follow this advice to the letter in order to prevent malicious apps from abusing the shared External Storage space to attack more potent apps.
Furthermore, researchers also feel that Android should also be hardened to prevent MitD attacks at the OS level, and not rely on app developers for putting these security measures up in the first place.
"From experience, it would seem that mere guidelines are not enough for OS vendors to exonerate themselves of all responsibility for what is designed by app developers. Instead, securing the underlying OS is the only long term solution to protecting against this new attack surface uncovered by our research," researchers said.
Check Point says it contacted Google and Xiaomi about the vulnerabilities it found in their apps. Google already released a patch for the affected apps while Xiaomi chose not to address the MitD attack vector.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now