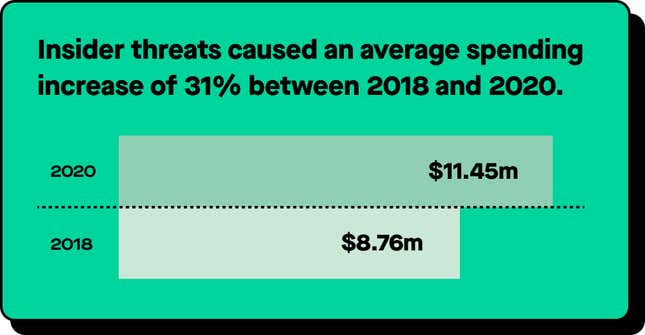
The abrupt shift from structured, contained workplaces to remote work has put more sensitive information in harm’s way. A single workforce might connect to multiple networks, accessing confidential materials on unauthorized devices, saving sensitive documents to personal USB drives and cloud storage, and leaving plenty of opportunities for insider risk or threats from within your organization overlooked. These threats can cause damage to your corporate reputation, cost millions to repair, and create a massive liability.
The good news: It is possible to give employees seamless information access while maintaining data security and regulatory compliance. Here’s a primer on how insider risk has significantly increased in the hybrid workplace, and what CISOs and other cybersecurity professionals can do about it.
The scope
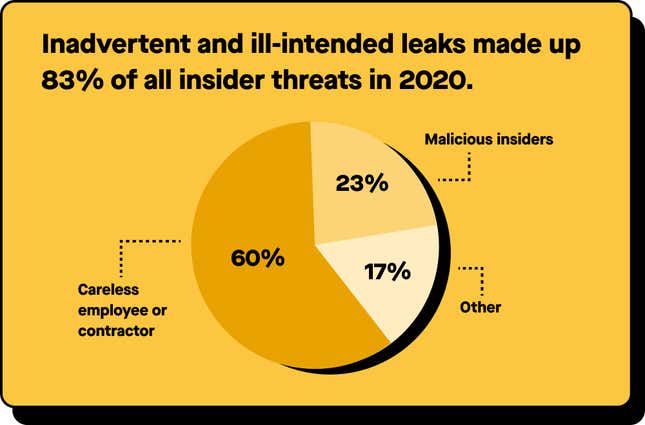
Insider risks can be sorted into two general categories: “malicious” and “inadvertent” leaks.
Ill-intended leaks: Leaks perpetrated by those with malicious objectives, such as IP theft when people leave the organization, or not-so-accidental confidentiality breaches.
Inadvertent leaks: Leaks that happen when employees are distracted or unaware of unsafe practices.
Plus, distraction and burnout are on the rise. One 2020 survey found remote workers labored an additional 3.13 hours per day. They are also often doing their jobs exclusively online, with increased meetings and calls per week, leading to mental exhaustion and burnout.
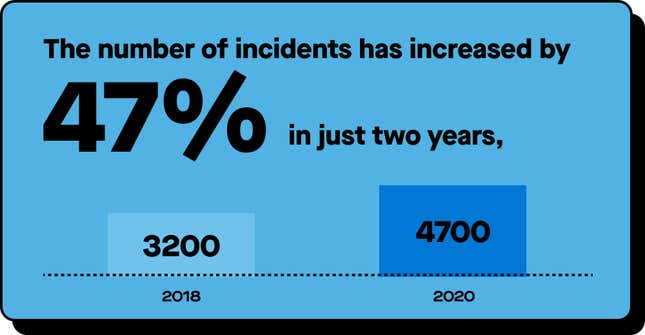
Data is only as secure as its handling, and with pressure mounting on workers, mistakes are bound to happen. Regardless of the intent, one thing is clear: Hybrid workplaces create new vulnerabilities to be exploited.
Businesses should organize their insider risk management around a three-pronged approach that keeps information-sharing friction-free while protecting nonpublic knowledge.
1. Establish a security-first culture
Even the most advanced security measures can’t succeed unless all of your employees feel trusted and empowered to protect the organization. Offer relevant training and transparent communication about their role in maintaining security, including protecting information, classifying data properly, and employing the appropriate protection platforms across their apps, platforms, and devices.
Your workers also need to be given a presumption of innocence; they don’t want to feel like they’re constantly under a microscope, or that their own privacy is being invaded. Build individual protection into your risk detection technology and ensure that when your employees log off for the day, their company device’s signal detection stops for the day, too. Your people are your allies, and you want to help them be collaborative and productive while ensuring that intelligence remains safe.
2. Adopt holistic solutions
Organizations must have a full view of all the places people are getting work done in order to have insights into other potential data sieves. We’re talking everywhere: on premises, in the cloud, across first- and third-party apps and collaboration services, and within browsers. The most effective systems use machine learning and analytics to correlate and examine sequences of signals and surface potential risks, allowing information security teams to quickly take action or investigate further and escalate appropriately. Also, organizations should look at systems that surface risks in a way that protects employee privacy through pseudonymization and strong access controls.
Another key element is teamwork across departments, such as IT, legal, and human resources. With the proper tools and support from all necessary teams, organizations can run safety measures in the background while keeping workflows intact for end users. They can also identify areas that require education, turning troubles into teachable moments.
3. Make responses proportional
We recently heard from a customer whose system uses machine learning to correlate and analyze signals, identifying activities that may point to heightened hazards. The day after launch, they received an alert related to potentially risky user behavior that they previously wouldn’t have discovered. It wasn’t a five-alarm fire—more like an ember that could have become something more. They doused it, released the necessary updates, and moved on.
When organizations have better visibility into insights and behaviors, they have a much clearer understanding of potential dangers. This allows leaders to remain calm when confronted with an issue, thus preventing impulsive or uninformed reactions, instead allowing them to take commensurate measures to safeguard their company. This level of control keeps things running smoothly and safely.
Read more: Securing and governing data in a new hybrid work reality
For more information on insider risk and data security strategies, check out the Microsoft Security Blog.
This content was produced on behalf of Microsoft by Quartz Creative and not by the Quartz editorial staff. Sources are provided for informational and reference purposes only. They are not an endorsement of Microsoft or Microsoft’s products or services.