
Japanese game developer Koei Tecmo has disclosed a data breach and taken their European and American websites offline after stolen data was posted to a hacker forum.
Koei Tecmo is known for its popular PC and console games, including Nioh 2, Hyrule Warriors, Atelier Ryza, Dead or Alive, etc.
On December 20th, a threat actor claimed to have hacked into the koeitecmoeurope.com website on December 18th through a spear-phishing campaign sent to an employee. As part of this attack, a forum database with 65,000 users was stolen, and the actor claims to have planted a web shell on the site for continued access.
"There are FTP credentials on the shell I found and I would be happy to share those with you if you bought the shell as well as multiple twitter secrets for their twitter accounts that they have," the threat actor stated as part of their sales pitch.
In a post on a hacker forum, the threat actor was attempting to sell a forum database for 0.05 bitcoins, or approximately $1,300, and web shell access for 0.25, or approximately $6,500.
On December 23rd, the same threat actor leaked the database for free on the same hacker forum.
The samples of the database seen by BleepingComputer include forum members' email addresses, IP addresses, hashed passwords and salts, usernames, date of births, and country.
Koei Tecmo takes websites offline
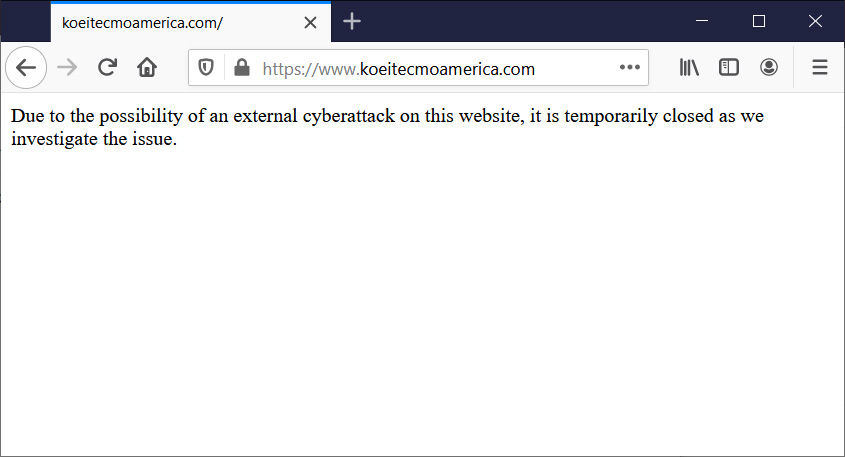
After learning of the leaked data, Koei Tecmo took the American (https://www.koeitecmoamerica.com/) and European (koeitecmoeurope.com) websites offline with the following message:
"Due to the possibility of an external cyberattack on this website, it is temporarily closed as we investigate the issue."
Since learning of the attack, Koei Tecmo released a data breach advisory stating that a forum on a UK subsidiary's website was compromised and the stolen data was leaked online.
"Within the website operated by KTE, the “Forum” page and the registered user information (approximately 65,000 entries) has been determined to the data that may have been breached. The user data that may have been leaked through hacking is perceived to be the (optional) account names and related password (encrypted) and/or registered e-mail address," Koei Tecmo disclosed in a data breach advisory.
Koei Tecmo states that the breach only affected the forum and not other portions of the site. They also say that no financial information was stored in this database.
The game company has determined "that the possibility of it being a ransomware attack is low" and that there have been no threats or demands made to the company.
Out of an abundance of caution, Koei Tecmo has cut off the UK subsidiary KTE from its internal network while investigating the attack.
Koei Tecmo is not the first game developer hit with a cyberattack this year.
Earlier this year, Crytek and Ubisoft were hit by the Egregor ransomware operation, and Capcom suffered a Ragnar Locker ransomware attack, where 1 TB of data was stolen.
Update 12/28/30: The hacker behind the breach contacted BleepingComputer and stated that they leaked the data because Koei Tecmo failed to follow GDPR guidelines.
I released it after they removed the web shell but had not let users know or had made GDPR aware within guidelines.
"From 25 May 2018, the General Data Protection Regulation (GDPR) introduces a requirement for organizations to report personal data breaches to the relevant supervisory authority, where the breach presents a risk to the affected individuals. Organizations must do this within 72 hours of becoming aware of the breach."
72 hours is key here and while I may not be the most ethical person, I care a lot when it comes to user security and privacy and if companies refuse to use simple encryption techniques to stop user data from the fallout of a cyber attack, I will keep attacking them. If they do not adhere to guidelines set by the people, they will face fallout.
They could spend just a few extra shekels to encrypt user information to ten rounds of bcrypt and WHEN, not IF there is a cyber attack users will be protected to an extent but they refused to do that over costs of processing power and instead chose to use a weak salted MD5 hashing algorithm from 1992. They refused to update their systems to divert a cyber attack, and that was their responsibility with 65,000 user records.


Comments
EmanuelJacobsson - 3 years ago
About time those perverted weebs got it.