
Microsoft has started enforcing number matching in Microsoft Authenticator push notifications to fend off multi-factor authentication (MFA) fatigue attacks.
In such attacks (also known as push bombing or MFA push spam), cybercriminals flood the targets with mobile push notifications asking them to approve attempts to log into their corporate accounts using stolen credentials.
In many cases, the targets will give in to the repeated malicious MFA push requests, either by mistake or to stop the seemingly endless stream of alerts, allowing the attackers to log into their accounts.
This type of social engineering attack has already been proven very successful by the Lapsus$ and Yanluowang threat actors who used this attack method to breach high-profile organizations, including Microsoft, Cisco, and Uber.
However, as previously announced, Microsoft will start enforcing number matching for Microsoft Authenticator MFA alerts to block MFA fatigue attack attempts across tenants beginning today.
"Number matching is a key security upgrade to traditional second factor notifications in Microsoft Authenticator. We will remove the admin controls and enforce the number match experience tenant-wide for all users of Microsoft Authenticator push notifications starting May 8, 2023," Microsoft says.
"Relevant services will begin deploying these changes after May 8, 2023 and users will start to see number match in approval requests. As services deploy, some may see number match while others don't."
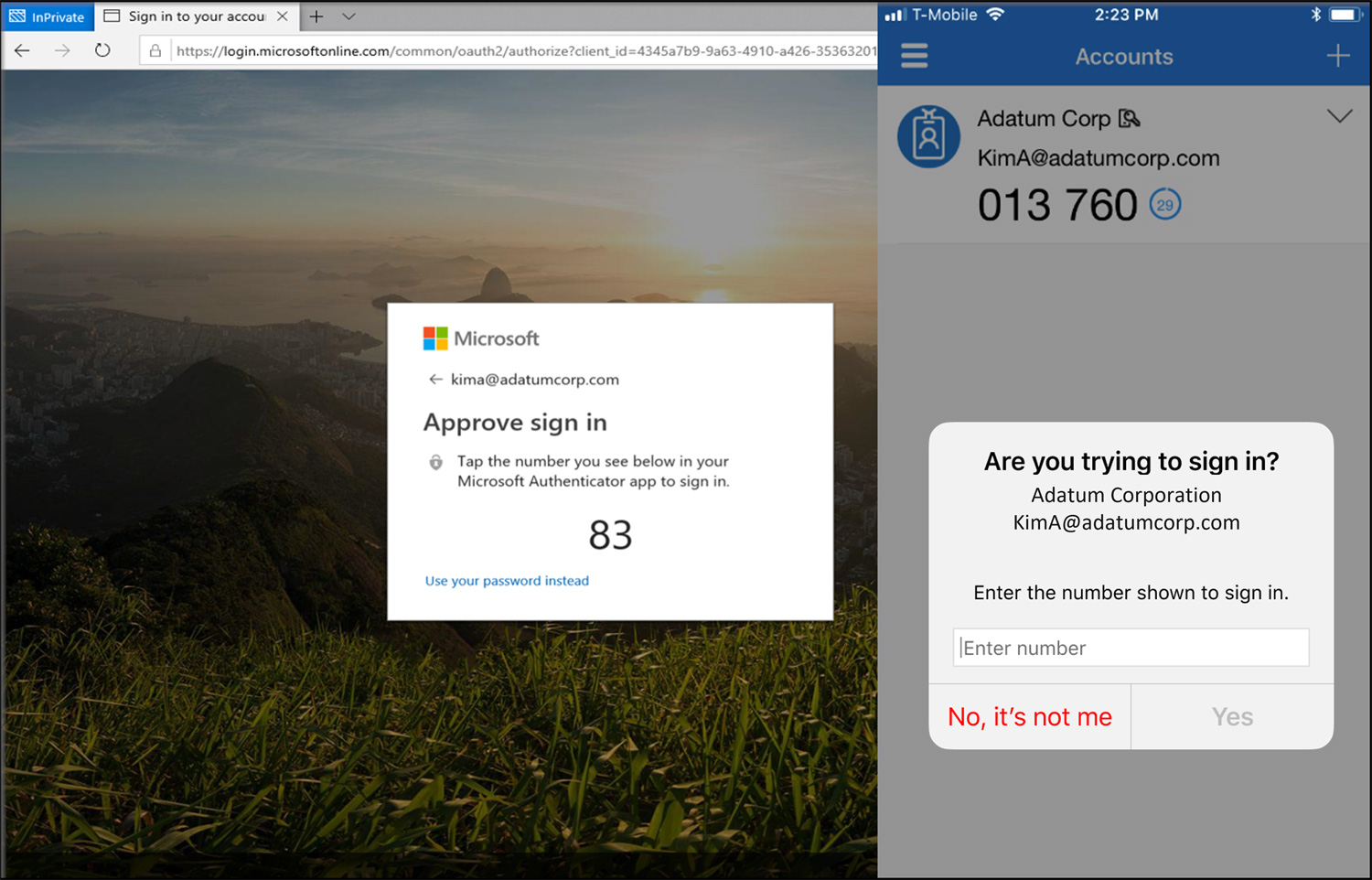
To manually enable number matching before Microsoft removes the admin controls, you have to go to Security > Authentication methods > Microsoft Authenticator in the Azure portal.
From there, go through the following steps:
- On the Enable and Target tab, click Yes and All users to enable the policy for everyone or add selected users and groups. Set the Authentication mode for these users/groups to Any or Push.
- On the Configure tab, for Require number matching for push notifications, change Status to Enabled, choose who to include or exclude from number matching, and click Save.
You can also enable number matching for all users or a single group with the help of Graph APIs (detailed info is available here).
"If the user has a different default authentication method, there won't be any change to their default sign-in," Microsoft says.
"If the default method is Microsoft Authenticator and the user is specified in either of the following policies, they'll start to receive number matching approval after May 8th, 2023."
Those who want to add an additional defense line against MFA fatigue attacks can also limit the number of MFA authentication requests per user (Microsoft, DUO, Okta) and lock the accounts or alert the security team/domain admin when those thresholds are exceeded.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now