
Toyota Boshoku Corporation, a car components manufacturer member of the Toyota Group, announced today that one of its European subsidiaries lost more than $37 million following a business email compromise (BEC) attack.
The company mentions in a press release published earlier today "a recent case involving fraudulent payment directions from a malicious third party that has resulted in a financial loss at our European subsidiary."
The expected financial loss following the incident that took place on August 14 is of roughly 4 billion yen maximum (as of 5 September), which translates to $37,472,000 (or €33,904,000).
BEC scam incident report to authorities
"Together with the European subsidiary, we became aware that the directions were fraudulent shortly after the leakage," further details Toyota Boshoku Corporation's press release.
After discovering the BEC fraud incident, the company started an investigation together with several legal professionals and subsequently disclosed the event to local authorities.
"While cooperating in all aspects of the investigation, we are devoting our utmost efforts to procedures for securing/recovering the leaked funds," adds the company. [PDF]
Other details are not yet available given the still-ongoing investigation, with the company planning to "disclose any amendments to the released March 2020 earnings forecast if this incident makes such revision necessary."
This incident follows a previous security breach disclosed by Toyota in March that impacted roughly 3.1 million customers whose personal information may have been leaked following a security breach of multiple Toyota and Lexus sales subsidiaries.
Australian Toyota dealers were also targeted by a cyber-attack which led to the shutdown of its corporate IT systems on February 19.
Highly profitable BEC scam operations
BEC (aka EAC, short for Email Account Compromise) fraud schemes are scam operations operated by fraudsters who attempt to deceive one or more employees of targeted organizations into wiring them money to bank accounts swapped with attacker-controlled ones.
This type of attacks is quite successful because of the crooks' choice to pose as individuals the employees trust such as a trusted business partner or the company's CEO.
BEC scams are highly prevalent, with similar incidents making the news almost on a daily basis. Fortunately, some BEC victims recover some of the stolen funds by freezing them if they're not moved out of traceable accounts by the scammers, as it was the case with the Portland Public Schools which recovered roughly $2.9 million lost in a BEC attack during August.
However, others are not that fortunate, only having rescued some of the money lost, with the City of Saskatoon getting scammed out of $1.04 million and being in the process of recovering most of it, while Cabarrus County from North Carolina lost $1,728,082.60 in July after wiring $2.5 million to scammers.
Other victims were even less lucky though, with the Saint Ambrose Catholic Parish losing $1.75 million and the City of Griffin, Georgia, being robbed of roughly $800,000 in similar attacks coordinated by crooks who moved the stolen funds before getting traced by the authorities.
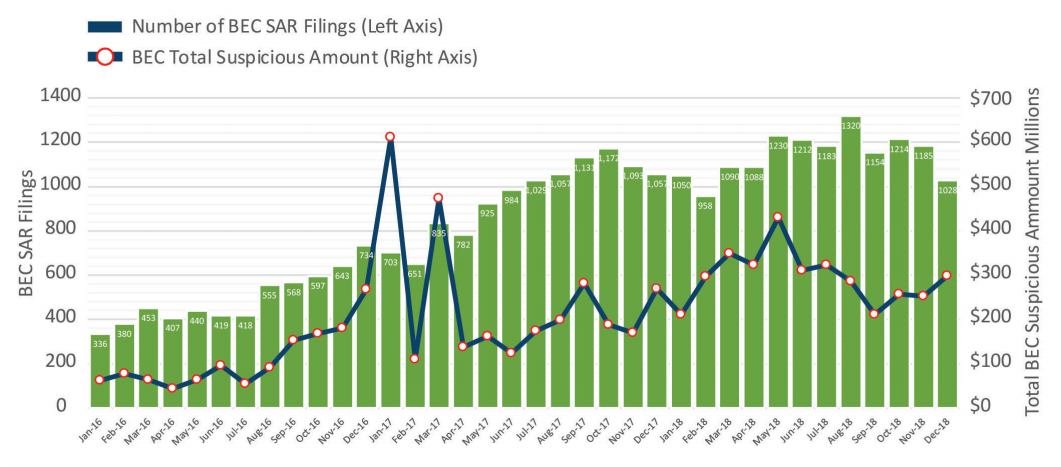
Overall, BEC victims lost over $1,2 billion during 2018 according to an Internet Crime report issued in April 2019 by FBI's Internet Crime Complaint Center (IC3).
The Financial Crimes Enforcement Network (FinCEN) also published a report in July saying that BEC SAR (short for suspicious activity reports) filings increased from a $110 million monthly average in 2016 to over $301 million per month in 2018.
To make sure that their employees won't get scammed in BEC attacks, companies have to use strict vendor processes to examine and authenticate payment info changes via multiple types of processes, including but not limited to face-to-face meetings and/or direct phone calls when any modifications to payment information are being detected.
BleepingComputer has reached out to Toyota Boshoku Corporation for mode details but had not heard back at the time of this publication. This article will be updated when a response is received.
Update September 09, 07:46 EDT: A Toyota Boshoku Corporation spokesperson sent BleepingComputer the following statement when asked about the date when the incident was discovered and if there is any chance to recover the money from the scammer's accounts:
As the criminal investigation is still ongoing, we would like to refrain from providing details on when the incident was discovered.
Given the time needed to confirm facts and go through the process of notifying related authority as well as potential impact on the criminal investigation and procedures for damage recovery, we decided to make the announcement as promptly as possible.
We are devoting our utmost efforts towards full recovery of the leaked funds.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now