A Twitterer sent me this a few days ago:
.@troyhunt you've got SSL issues in Chrome 58+ on @ASafaWeb pic.twitter.com/qtUiMxV9tW
— Jonathan (@Eonasdan) April 13, 2017
Now normally when I get a report about an SSL thing not working (by which we mean TLS, but we say SSL anyway), I jump on over to SSL Labs (see?!) and run a report I can then direct people to. This usually provides emphatic proof that the SSL configuration is fine and they've just got an old client or some funky MitM stuff going on in their local network. However, this time was different:
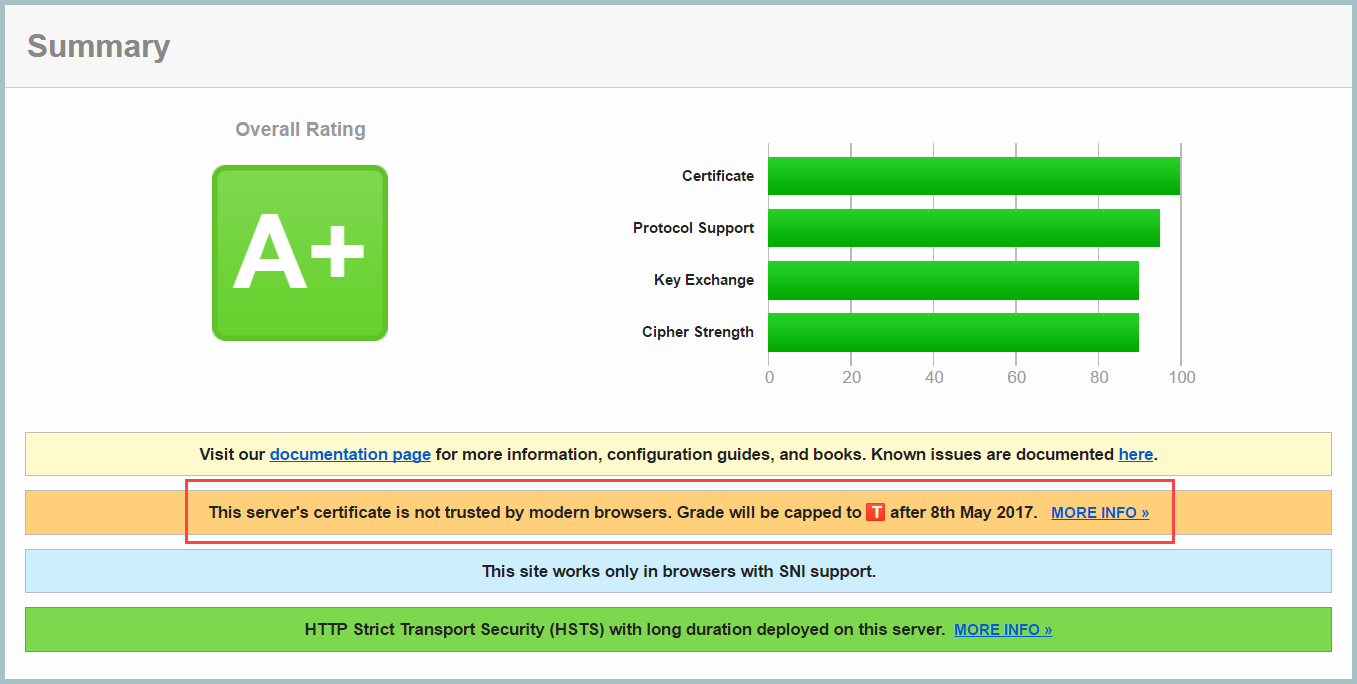
"Grade will be capped to T". Now I didn't immediately realise what "T" was, but I know it's lower than "F" and that's bad! But one look at the link on that row and the penny dropped - it's the WoSign debacle. This goes back to them doing a bunch of dodgy things last year, amongst which was the way they acquired StartCom, the CA whose cert I was using on ASafaWeb:
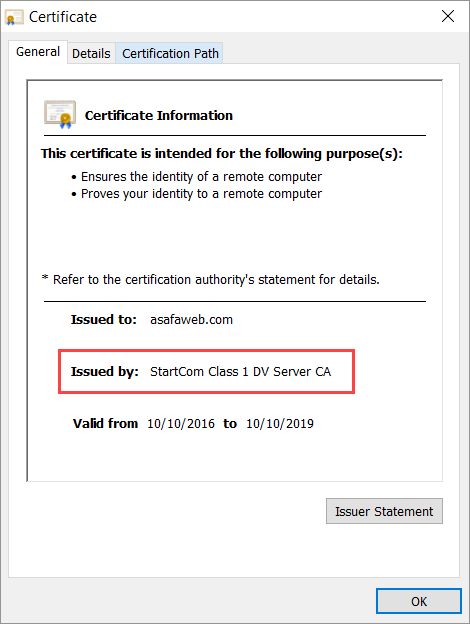
As detailed in the explanation of the "T" grade:
From 8 May 2017 such certificates will be graded with a T (no trust)
What Jonathan was seeing in that earlier tweet was the next version of Chrome distrusting the cert and indeed Google have been flagging this for some time now. As you can see from the date in the cert above, I obtained it from StartCom just before the whole WoSign situation. If I had grabbed it only a couple of weeks later then it would have been distrusted as of Chrome 56 which shipped back in Jan. Instead, ASafaWeb falls into this category:
In subsequent Chrome releases, these exceptions will be reduced and ultimately removed, culminating in the full distrust of these CAs
I knew this, but honestly hadn't given it any more thought since reading it. ASafaWeb is frankly just in maintenance mode these days anyway so I rarely touch it, but so are many other sites on the web hence why I thought writing this post as a little reminder would make sense.
In terms of migrating away, I still run ASafaWeb on AppHarbor and use their PaaS hosting model. I have no shell access to the machine and they have no Let's Encrypt integration exposed via a UI, but frankly I prefer Cloudflare anyway for all the other features it gives me and like Let's Encrypt, it's free. So it's over to Cloudflare, add the site and then in a fraction of the time it's taken me to write this blog post, it's job done:
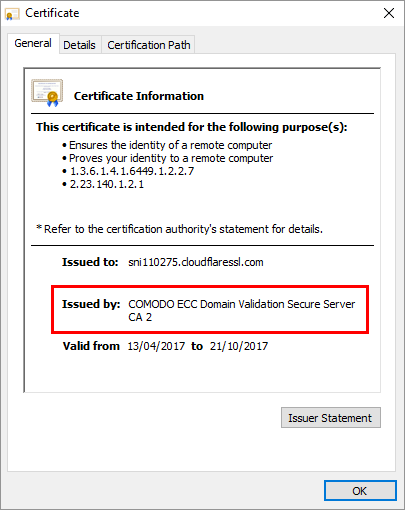
So that I can keep the connection from Cloudflare to ASafaWeb fully encrypted and not have to worry about them not trusting StartCom or having to put another cert on the origin later on, I issued one of their free Origin CA certs and loaded that into AppHarbor.
If you use a StartCom cert on your site, you need to replace it now.
It can be an easy job and if you don't do it soon, you're about to start hearing about it from your customers! And if you're reading this and thinking "wow, it'd be worthwhile learning a bit about some of these SSL nuances", last week my Pluralsight course on What Every Developer Must Know About HTTPS went live so check that out. As this example shows, it's easy to screw this up so it's well worth brushing up on your SSL / TLS / HTTPS things if you're not already well and truly on top of them.