
A security advisory for a vulnerability (CVE) published by MITRE has accidentally been exposing links to remote admin consoles of over a dozen vulnerable IP devices since at least April 2022.
BleepingComputer became aware of this issue yesterday after getting tipped off by a reader who prefers to remain anonymous. The reader was baffled on seeing several links to vulnerable systems listed within the "references" section of the CVE advisory.
CVE advisories published by MITRE get syndicated verbatim across a large number of public sources, feeds, infosec news sites, and vendors providing this data to their customers.
The "references" section of these advisories typically lists links to the original source (a writeup, blog post, PoC demo) that explains the vulnerability. However, including links to publicly exposed unpatched systems can potentially allow threat actors to now target these systems and conduct their malicious activities.
BleepingComputer conducted some additional investigation as to how this issue may have occurred and reached out to MITRE as well as some security experts to better understand if this is a normal, or even acceptable, practice.
Security advisory spills the beans
A vulnerability advisory published by MITRE for a high-severity information disclosure vulnerability in April ironically disclosed links to over a dozen live IoT devices vulnerable to the flaw.
It isn't unusual for security advisories to include a "reference" section with several links that validate the existence of a vulnerability. But, any such links typically lead to a proof of concept (PoC) demonstration or writeups explaining the vulnerability rather than to vulnerable systems themselves.
After vulnerabilities are made public, attackers use public IoT search engines like Shodan or Censys to hunt for and target vulnerable devices.
All of which makes this a particularly uncanny case for a public security bulletin to list not one but locations of several vulnerable devices that are still connected to the internet.
Because a large number of sources rely on MITRE and NVD/NIST for receiving vulnerability feeds, the CVE advisory (redacted below) has already been syndicated by several vendors, public sources, and services providing CVE data, as observed by BleepingComputer.
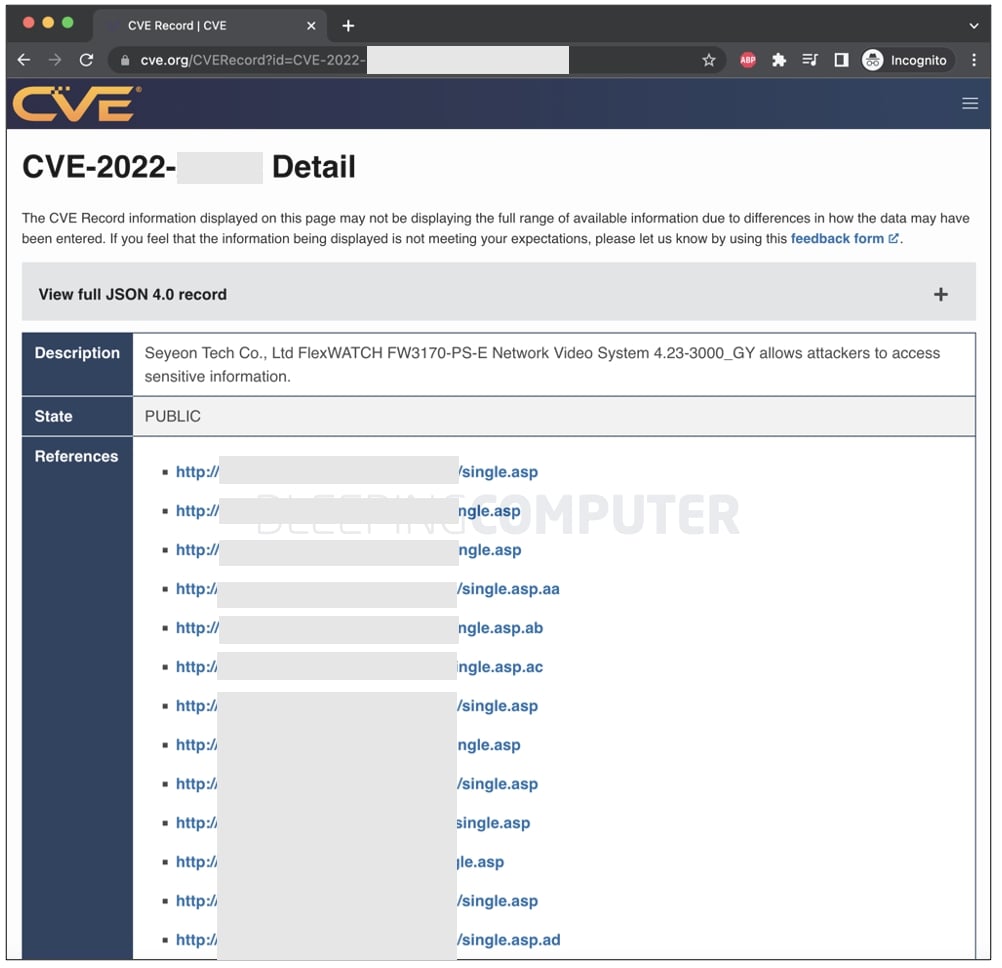
Clicking on any of the above "reference" links would lead the user to a remote administration dashboard of the (vulnerable) IP cameras or video devices, potentially allowing them to view the live camera feed or exploit the vulnerability.
Note, BleepingComputer did not perform any kind of penetration test or further engage with these links other than ensuring these were live and immediately notified MITRE of the issue.
MITRE: What's wrong? We've done it before
BleepingComputer notified MITRE yesterday of this issue and why this could be a security concern.
Surprisingly, we were asked by MITRE, why did we "think these sites should not be included in the advisory," and were further told that MITRE had, in the past, "often listed URLs or other points that may be vulnerable" in similar CVE entries.
MITRE's response prompted BleepingComputer to further contact security experts.
Will Dormann, a vulnerability analyst at the CERT Coordination Center (CERT/CC) called this "both not normal and a very BAD thing" to do. And, security researcher Jonathan Leitschuh said much the same in a statement to BleepingComputer.
"It's disrespectful to the affected parties to list live vulnerable instances within a CVE entry," Dormann tells BleepingComputer.
"The parties involved in the creation of CVE entries should know better. Somewhat surprisingly, according to the GitHub repo for CVE-2022-..., the author was MITRE themselves."
It is true the CVE advisory itself was published by MITRE, the parent organization of the CVE project that is often the first point of contact for users reporting security vulnerabilities in third-party systems and requesting CVE identifiers.
But, BleepingComputer discovered the original source of the mishap was a security writeup published by one or more Chinese security researchers on GitHub while MITRE's CVE entry for the vulnerability had been "reserved" and awaiting production.
It is in this GitHub version of the advisory that several links to vulnerable devices were listed as "examples." And this information appears to have been copied-pasted in the MITRE's CVE entry that was later syndicated across several sites:
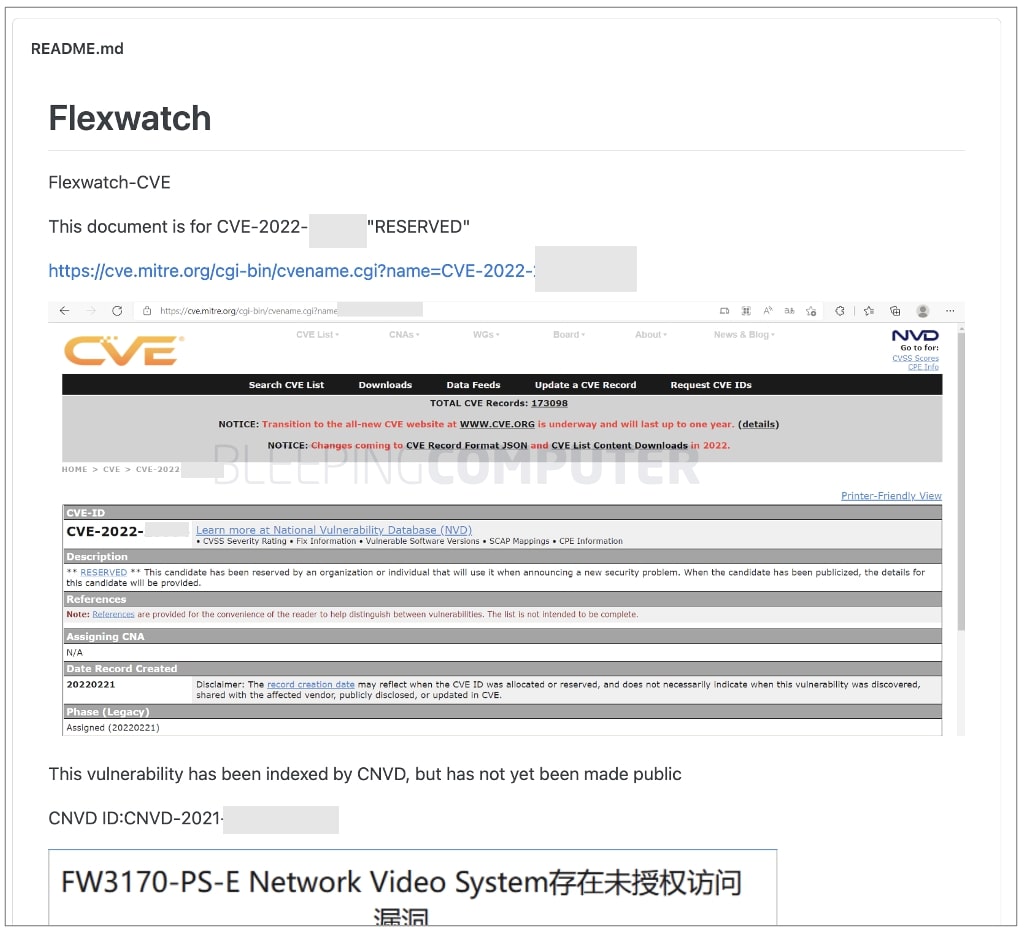
Ironically, the original advisory published to GitHub has long been deleted.
Dormann further added, "I just copied and pasted somebody else's work" isn't really a valid excuse and "not living up to MITRE's standards."
It seems this isn't the only time MITRE's CVE database has fallen short of validating links provided in its advisories or retroactively removing dead links:
Hey @CVEannounce there are 2031 mandriva .com URLs in 4,530 CVE entries that are all dead now and lead to an unsafe site advertising online casinos. Please clean up your data. Thanks pic.twitter.com/rIkxWBE1rD
— Kurt Seifried (He/Him) (@kurtseifried) July 4, 2022
Note, within a few hours of our email to MITRE, the CVE advisory was swiftly updated to remove all "reference" links pointing to vulnerable IoT devices, from both MITRE's CVEProject GitHub repo and the database. But this update may not remove this information from third-party sources that have already retrieved and published an earlier copy of the entry.
When publishing security bulletins and vulnerability advisories, caution must be exercised to ensure only necessary information about a vulnerability is revealed to help defenders action the security flaws, without inadvertently aiding malicious actors.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now