
After the ransacking of MongoDB, ElasticSearch, Hadoop, CouchDB, and Cassandra servers, attackers are now hijacking hundreds of MySQL databases, deleting their content, and leaving a ransom note behind asking for a 0.2 Bitcoin ($235) payment.
According to breach detection firm GuardiCore, the attacks are happening via brute-force attacks on Internet-exposed MySQL servers, and there's plenty of those laying around since MySQL is one of today's most popular database systems.
All attacks came from a server in the Netherlands
Based on currently available evidence, the attacks started on February 12, and only lasted for 30 hours, during which time attackers attempted to brute-force their way into MySQL root accounts.
Investigators said all attacks came from the same IP address from the Netherlands, 109.236.88.20, belonging to a hosting company called WorldStream.
During their ransacking, attackers didn't behave in a constant pattern, making it hard to attribute the hacks to one group, despite the usage of the same IP.
For example, after gaining access to MySQL servers, attackers created a new database called PLEASE_READ and left a table inside it called WARNING that contained their ransom demands. In some cases, attackers only created the WARNING table and left it inside an already existing database, without creating a new one.
Investigators report that attackers would then dump the database's content and delete it afterward, leaving only the one holding their ransom. In some cases, attackers deleted the databases without dumping any data.
Attackers have their own website
Two ransom notes have been found in the hundreds of confirmed attacks, one asking victims to get in contact via email and confirm the payment, while the other used a completely different mode of operation, redirecting users to a Tor-hosted website.
INSERT INTO PLEASE_READ.`WARNING`(id, warning, Bitcoin_Address, Email) VALUES(‘1′,’Send 0.2 BTC to this address and contact this email with your ip or db_name of your server to recover your database! Your DB is Backed up to our servers!’, ‘1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY’, ‘backupservice@mail2tor.com’)
INSERT INTO `WARNING`(id, warning)
VALUES(1, ‘SEND 0.2 BTC TO THIS ADDRESS 1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9 AND GO TO THIS SITE http://sognd75g4isasu2v.onion/ TO RECOVER YOUR DATABASE! SQL DUMP WILL BE AVAILABLE AFTER PAYMENT! To access this site you have use the tor browser https://www.torproject.org/projects/torbrowser.html.en’)
At the time of writing, the Tor website is still up and running.
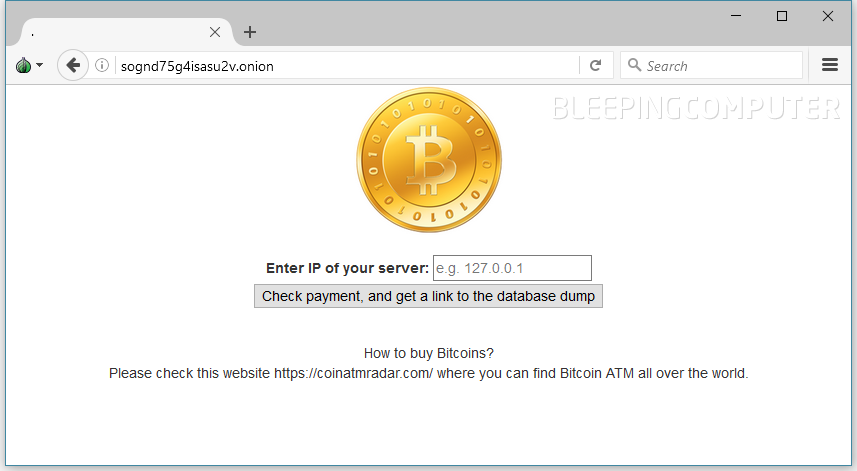
The two Bitcoin addresses listed in the ransom notes received four and six payments, respectively, albeit GuardiCore experts doubt that all are from victims.
"[W]e can not tell whether it was the attackers who made the transactions to make their victims feel more confident about paying," they said.
Be sure the attacker still has your data
Just like in the case of the now infamous MongoDB attacks that have hit over 41,000 servers, it's recommended that victims check logs before deciding to pay and see if the attackers actually took their data.
If companies elect to pay the ransom, should always ask the attacker for proof they still have their data.
None of this would be an issue if IT teams follow standard security practices that involve using an automated server backup system and deleting the MySQL root account or at least using a strong and hard-to-brute-force password.
This is not the first time MySQL servers have been held for ransom. The same thing happened in 2015, in a series of attacks called RansomWeb, where attackers used unpatched phpBB forums to hijack databases and hold websites up for ransom.


Comments
Demonslay335 - 7 years ago
MySQL shouldn't even be exposed to the internet really... most setups will have it on localhost only, and in the case of it being on another server, you should have it behind a firewall or have some sort of way of restricting IPs to login from. I don't think privileges for root to login from anything but localhost is enabled by default, atleast from my experience in setting up MySQL 5.4 on Windows and Ubuntu boxes.
DodoIso - 7 years ago
1
DodoIso - 7 years ago
... Plus 1