
Scammers can collect highly sensitive information about a company's activity, employees, and clients, even if after it shuts down, a cybersecurity expert warns.
Gabor Szathmari explored the risks associated with domain name abandonment and found that he could use them to retrieve emails with sensitive information, account passwords, to take over accounts for popular online services, or to access profession-specific portals.
When a domain name expires, it does not become immediately available for purchase. It moves into a reserved state that allows its previous owner to reclaim it. The grace period is typically 30 days, but this may vary for each registrar.
Multiple online services provide lists with domains that the registrar has dropped and are accessible for purchase at no extra cost, so one can target specific businesses.
A small team of researchers with Szathmari at the helm acquired six abandoned domain names, some of them formerly owned by Australian legal practices.
Owning them means control over the email flow, including the messages that intended for the former business. Setting up a catch-all email service allows the scammer to collect emails for any address on the domain in a general inbox.
Once the emails started pouring in, the researchers could glean details that would be perfect for a fraudster. They ended up with about 25,000 messages containing reports, statement, notifications, newsletters and, above all, spam.
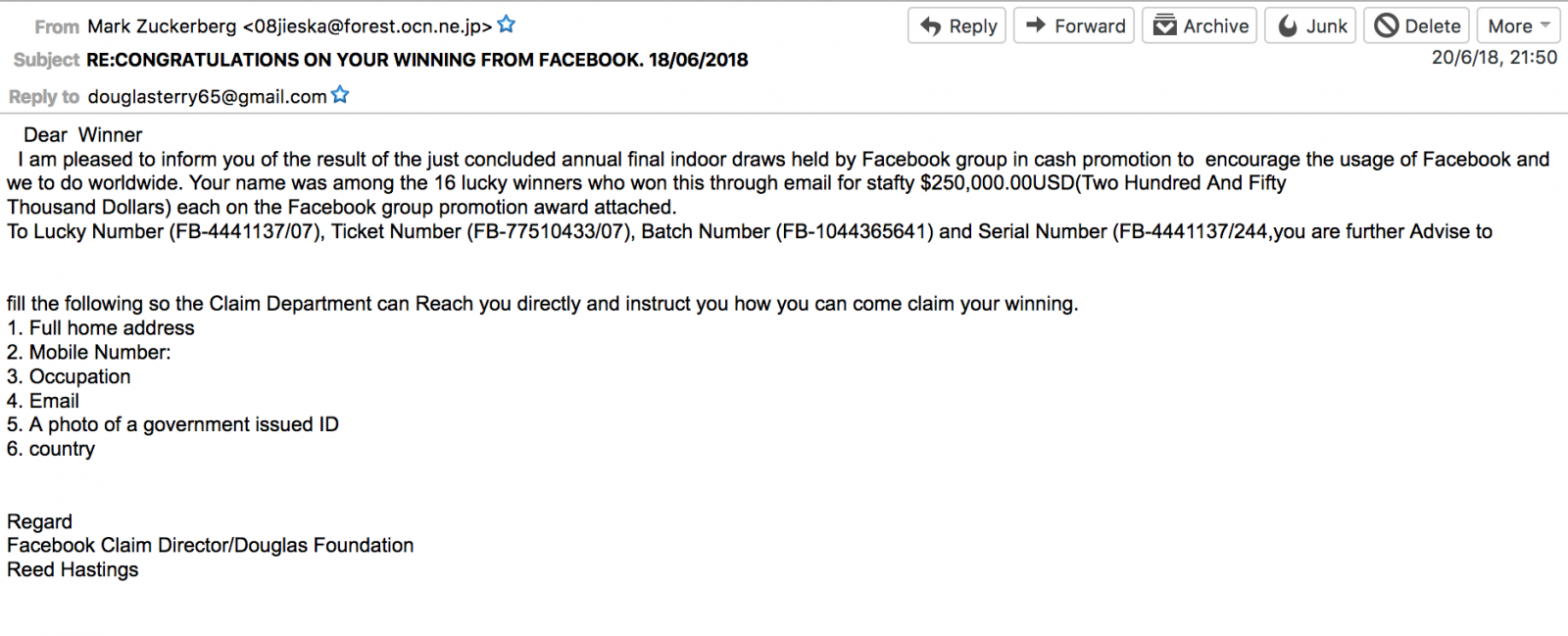
"We spent hours and hours skimming through the rubbish for finding gems for the report," Szathmari wrote in an email to Bleeping Computer.
To help with sorting out irrelevant content the team developed a talent for spotting spam, but later relied on DNS-based Blackhole Lists (DNSBL) services from two providers, Spamhaus and Barracuda Reputation Block List.
Hijacking company's cloud-based resources
A working email address is a requirement for initiating password resets for most online services, and could work for changing the access credentials for the former business and its staff.
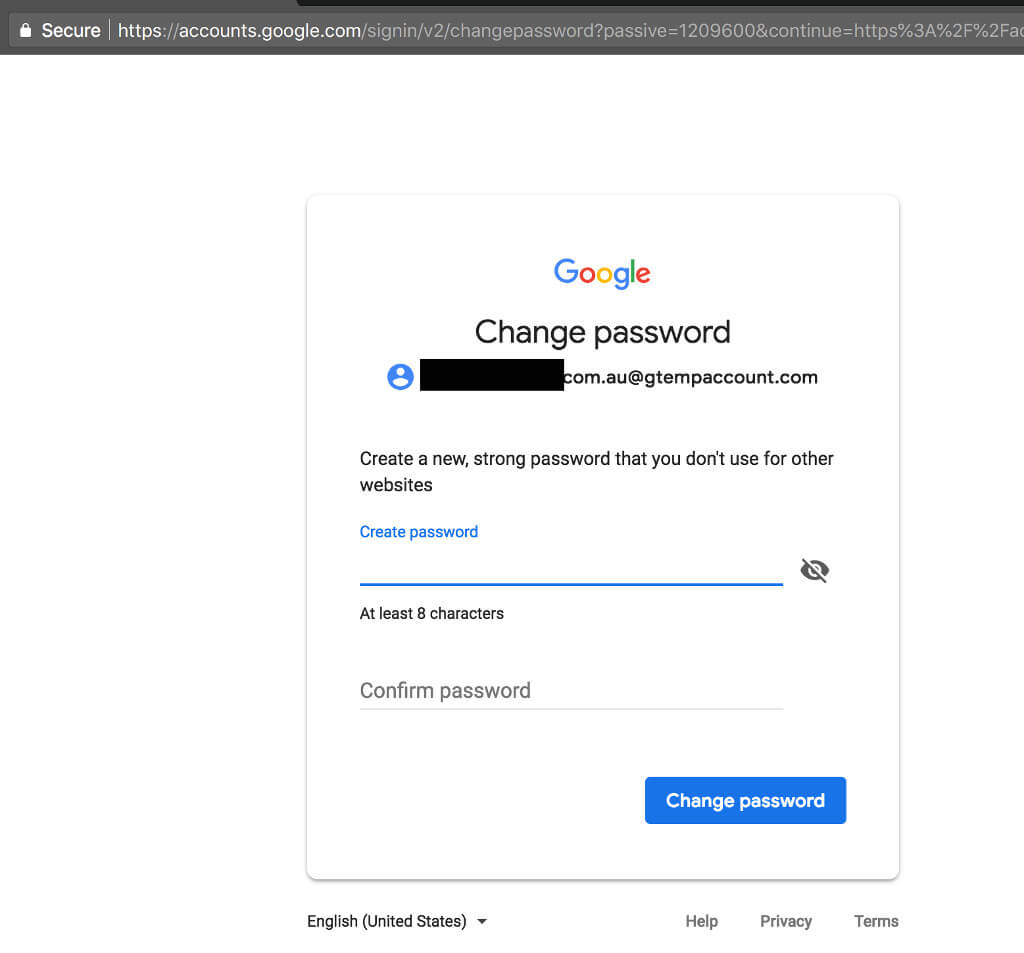
Office 365 and G Suite are two platforms many businesses use at least for handling email communication. Unless users delete the messages from the cloud, they stay available for anyone who can log in.
The researchers tried to get access to the G Suite account associated with a domain they controlled, and successfully went through all the steps leading up to resetting the password.
"We stopped at this last step and decided to not complete the password reset process on G Suite," Szathmari wrote.
Pwning personal social media accounts
Since employees often use business emails for personal purposes, their accounts were at risk of hijacking, too. Szathmari found that some practitioners used their work address to sign up on Twitter, Facebook, and LinkedIn.
Websites like SpyCloud and Have I Been Pwned let domain owners check the data breaches that included any of their accounts. The researchers used these services to retrieve former emails and passwords.
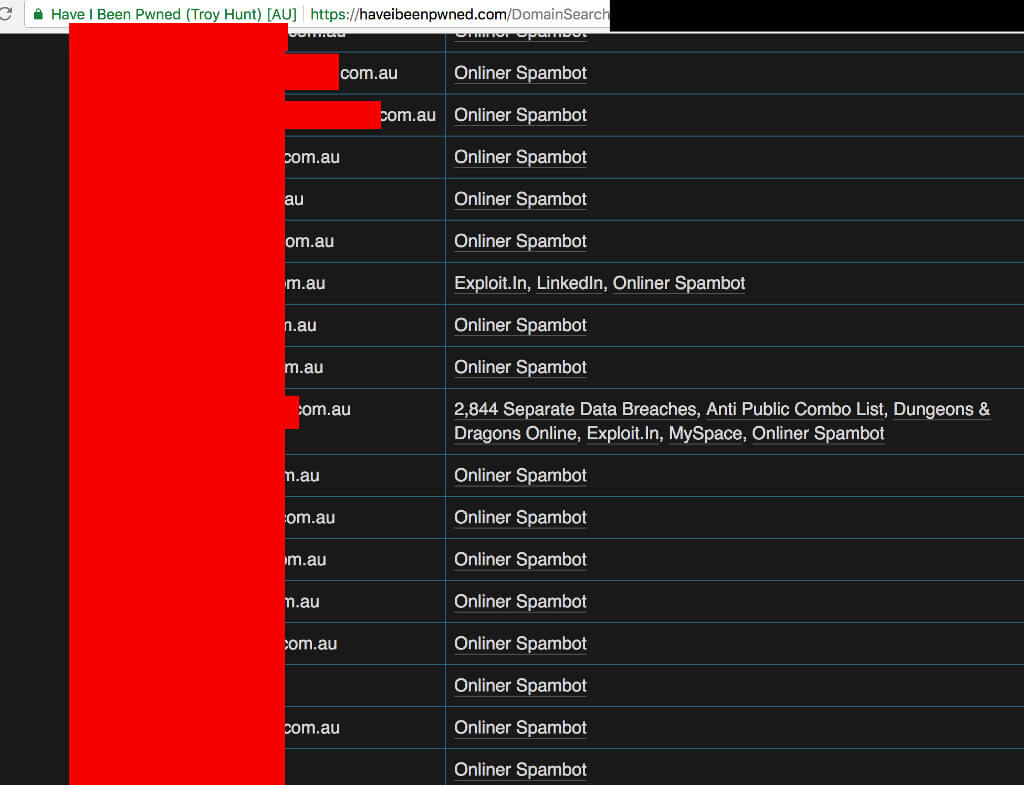
"By having the list of valid email addresses taken from Haveibeenpwned, we can demonstrate how we could have taken control over the current personal and work-related user accounts of former staff," Szathmary says.
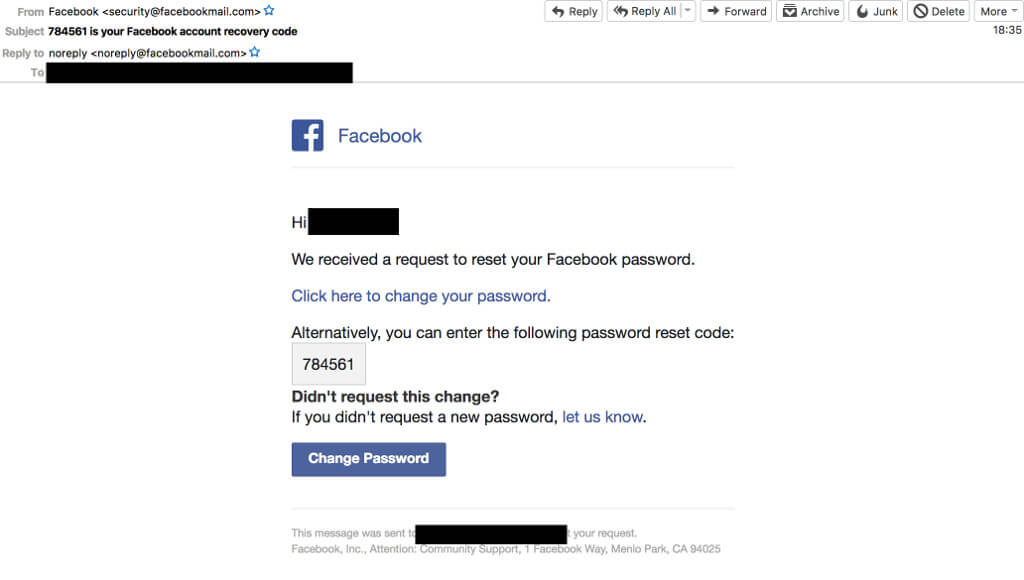
On LinkedIn, users can request a password reset to any of the addresses tied to the account. If the abandoned address is still on the list, changing the login credentials is easy.

The researchers followed the same routine for Twitter and Facebook and obtained a password reset email they could have used to lock the account owner out.

The forgotten password feature also worked with web profession-specific web portals. One by one, the Commonwealth Courts Portal, the LEAP Practice Management Platform, and the NSW Online Registry portal fell for the same trick.
Preventative measures
The simplest way to defend against this type of abuse is to make sure that the domain is valid for an indefinite period, even if the company no longer uses it.
Unsubscribing from notifications that include sensitive details is an obvious course of action, following Szathmari's revelations.
Closing the accounts that use the business emails, or at least disassociating them, is also a solution, albeit not all employees may heed the request.
Two-factor authentication is a good protection against account hijacking as it requires both the password for the account as well as a secret code delivered to a device in the possession of the owner. In many cases, the fraudster is unable to get both.


Comments
gabors - 5 years ago
This is one of the researchers here. We have published a few practical tips here for individuals and small businesses to help them avoid being a victim of abandoned domains: https://blog.ironbastion.com.au/abandoned-domain-names-are-risk-to-businesses/