 A hacker who goes online only by the pseudonym of Xerub has released the decryption key for Apple's Secure Enclave Processor (SEP) firmware.
A hacker who goes online only by the pseudonym of Xerub has released the decryption key for Apple's Secure Enclave Processor (SEP) firmware.
The leak, confirmed by an Apple employee who wanted to remain anonymous, is crucial to iOS security, as it now allows hackers and security researchers alike access to a previously encrypted iOS component.
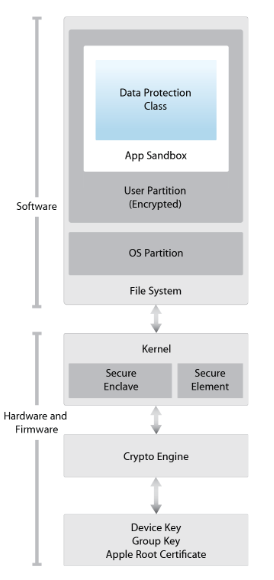
SEP handles TouchID operations, some iOS crypto
Apple describes SEP in its official security guide as a separate processor that sits next to the main CPU. This SEP coprocessor runs its own low-level operating system, has a separate update process, its own secure boot system, only uses encrypted memory, and includes its own hardware random number generator (RNG).
According to Apple, SEP was deployed starting with Apple S2, Apple A7, and later A-series processors, and is used to handle cryptographic data, and was later used to verify TouchID (fingerprint) transactions.
On Wednesday, Xerub published the encryption key that protects the SEP firmware. The key is available here.
key is fully grown https://t.co/MwN4kb9SQI use https://t.co/I9fLo5Iglh to decrypt and https://t.co/og6tiJHbCu to process
— ~ (@xerub) August 16, 2017
No user data in danger (yet)
This key allows someone to decrypt the SEP firmware. It does not allow a third-party to decrypt and access TouchID or other data passing through SEP.
Xerub's discovery is not inherently dangerous in itself, but through the ripples caused in the world of iOS security.
A publicly available SEP decryption key will allow hackers, surveillance companies, and others to analyze and look for bugs in an area of iOS devices they previously had not had access to.
New exploits could be developed that could bypass fingerprint authentication to access locked devices or approve fraudulent financial transactions via payment solutions like Apple Pay, and others.
Until now, researchers only speculated about what was happening inside SEP. The most insightful research on this topic is titled "Demystifying the Secure Enclave Processor" [PDF, YouTube], and was presented last year at Black Hat Europe.
iOS 11 adds a panic button
On a side note, the next iOS version — iOS 11, currently in beta — includes a "panic button" feature that forces passphrase entry on top of TouchID verification by pressing the Power button five times in a rapid succession.
The thinking behind this new feature is to force the phone from TouchID to passphrase entry in situations where the device owner might be physically forced to put his finger on the TouchID sensor.
iOS 11 is a game-changer for Touch ID. Press power button rapidly 5 times and it opens the 2nd screen, but it also forces passphrase entry! pic.twitter.com/uvWbM04lyk
— Kia☆ (@alt_kia) August 17, 2017


Comments
eq2675 - 6 years ago
Is this the processor that Edward Snowden was referring to?