
Today, the Akira ransomware gang claimed that it breached the network of Nissan Australia, the Australian division of Japanese car maker Nissan.
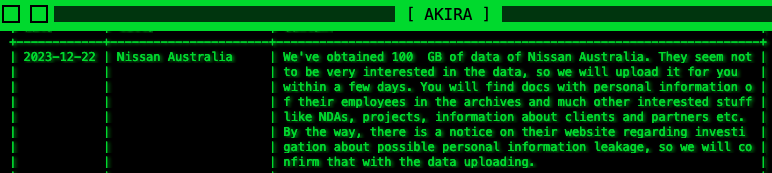
In a new entry added to the operation's date leak blog on December 22, Akira says that its operators allegedly stole around 100GB of documents from the automaker's systems.
The attackers have threatened to leak sensitive business and client data online, as ransom negotiations with Nissan failed after the company either refused to engage or pay the ransom.
"They seem not to be very interested in the data, so we will upload it for you within a few days," the ransomware group says. "You will find docs with personal information of their employees in the archives and much other interested stuff like NDAs, projects, information about clients and partners etc."
Akira surfaced in March 2023 and drew attention after quickly amassing a large number of victims from various industry sectors.
In June 2023, Akira ransomware operators started deploying a Linux variant of their encryptor designed to target VMware ESXi virtual machines widely used in enterprise environments.
According to negotiations seen by BleepingComputer, the ransomware group is asking for ransom payments from $200,000 to millions of dollars, depending on the breached organization's size.
While another ransomware strain named Akira was released five years ago, in 2017, the two operations are unlikely to be related.
Nissan still working to restore systems
While the company has yet to attribute a cyberattack disclosed on December 5, it did add a new update to its website today confirming that attackers have breached some of its systems in Australia and New Zealand.
Nissan says it's still investigating the incident's impact and whether personal information has been accessed. It's also working on restoring systems affected in the attack (a process that started on December 5, after the incident was disclosed.
"We cannot yet confirm the extent of the cyber incident. We are working with our global incident response team and cybersecurity experts to investigate the incident as a matter of urgency," Nissan said.
"Some dealer systems will be impacted however, your local Nissan Dealership is operating. Please speak directly to your local Nissan dealer to assist with all vehicle and servicing queries."
After detecting the breach, Nissan notified the Australian and the New Zealand Cyber Security Centres and relevant privacy regulators and law enforcement bodies.
Likely because of the risk that some data stored on the compromised systems was either accessed or stolen, Nissan also warned customers to "be vigilant for any unusual or suspicious online activity."
Nissan has yet to reply to a request for comment and additional information on the cyber incident from BleepingComputer.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now