Security researchers from Abuse.ch, BrillantIT, and Proofpoint have sinkholed the command and control infrastructure behind EITest, a network of hacked servers abused by cyber-criminals to redirect users to malware, exploits kits, and tech support scams.
EITest, considered the "king of traffic distribution," is a collection of compromised servers on which hackers have installed backdoors. Crooks use these backdoors to siphon off legitimate traffic from these sites and redirect users to malicious web pages.
This type of malicious activity is called "traffic distribution," and many cyber-criminals build such botnets of hacked sites and then rent it to fellow crooks who do with the traffic what they wish.
EITest appeared in 2011, became a rentable TDS in July 2014
EITest first appeared on the cyber-criminal market in 2011, and initially, it was not a rentable traffic distribution system. Its authors used it primarily to drive traffic towards their homegrown exploit kit known as Glazunov, which they used to infect users with the Zaccess trojan.
At the time, this was never a massive threat. EITest operators got smart about their operation in late 2013 when they started to rework their infrastructure, and by July 2014, they began renting out EITest to other malware authors.
According to Proofpoint researcher Kafeine, the EITest team started selling hijacked traffic from hacked sites for $20 per 1,000 users, selling traffic blocks of a minimum size of 50,000 users.
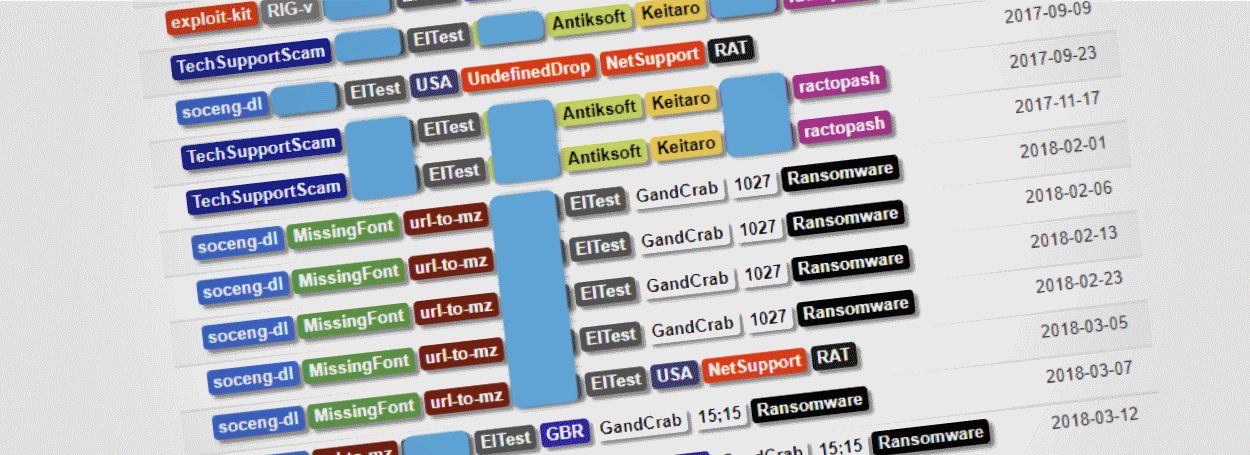
Ever since then, EITest has been a pain for security researchers on a daily basis, being involved in the distribution of countless ransomware families, redirecting huge swaths of traffic towards the Angler and RIG exploit kits, and recently in sending waves of users towards social engineering sites (browser lockers, tech support scams, fake updates, fake font packs).
Security firms sinkhole key EITest domain
However, the good guys caught a lucky break earlier this year, when a BrillantIT researcher managed to crack the way in which infected sites would connect to the command and control infrastructure.
By seizing one domain (stat-dns.com), they managed to hijack the entire EITest operation. That server has been pointing to a sinkhole since March 15, sparing millions of users from landing on malicious sites.
After analyzing the traffic flowing into the sinkhole, researchers got an insight into EITest's massive operation, revealing that the botnet handled about two million users per day coming from over 52,000 hacked websites, most of which were WordPress sites.
Not attempts to take back control of EITest network
"Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest," Proofpoint says.
For now, EITest's authors appear to have given up on trying to retake control over their former network, but this doesn't rule out them building a new one.
Besides EITest, other traffic distribution networks still exist on the market, such as Fobos, Ngay, and Seamless, while two other players —Afraidgate and pseudo-Darkleech— have been dormant for a few months.


Comments
backfolder - 6 years ago
Abuse.ch, BrillantIT, and Proofpoint...Thanks so much!!!