WikiLeaks published the first-ever batch of source code for CIA cyber-weapons. The source code released today is for a toolkit named Hive, a so-called implant framework, a system that allows CIA operatives to control the malware it deploys on infected computers.
From March to August this year, WikiLeaks has released only documentation for supposed CIA cyber-weapons the organization claims were stolen from the CIA by hackers and insiders, and then handed over to its employees.
WikiLeaks announces "Vault 8"
Those releases were part of a series of leaks WikiLeaks called Vault 7. Now, WikiLeaks says Hive is just the first of a long string of similar releases, a series WikiLeaks calls Vault 8, which will consist of source code for tools previously released in the Vault 7 series.
The WikiLeaks announcement has sent shivers up the spines of infosec experts everywhere, as it reminded them of April this year when a hacking group named The Shadow Brokers published cyber-weapons allegedly stolen from the NSA.
Some of the tools included in that release have been incorporated in many malware families and have been at the center of all three major ransomware outbreaks that have taken place n 2017 — WannaCry, NotPetya, and Bad Rabbit.
One particular tool released in the Shadow Brokers dump was FuzzBunch, a tool similar to Hive, an exploit and implant framework.
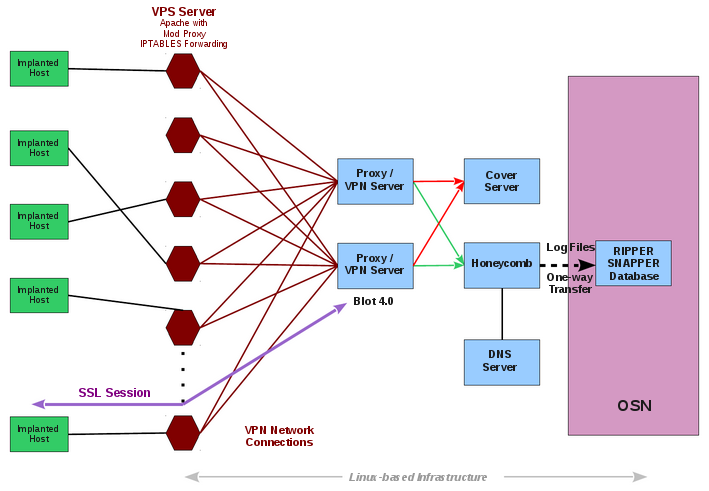
Hive does not possess danger to end users
Both tools do not possess an immediate danger to end users, as they cannot be used to compromise computers, but they can be used to set up a backbone infrastructure for the delivery and control of other more potent threats.
If WikiLeaks ends up releasing the source code of other Vault 7 tools, things could become tremendously worse for the rest of the world.
For example, tools like Achilles, Aeris, SeaPea, DarkSeaSkies, Archimedes, Brutal Kangaroo, or CherryBlossom, are actually offensive cyber-weapons that could be incorporated into various existing malware families and hacking toolsets. Hopefully, the organization will use caution and will not release tools that can be easily weaponized and the world can avoid a WannaCry ransomware outbreak, CIA edition.
Below is a list of the most important CIA cyber-weapons released by WikiLeaks as part of the Vault 7 series.
ᗙ Fine Dining - a collection of fake, malware-laced apps
ᗙ Grasshopper - a builder for Windows malware
ᗙ DarkSeaSkies - tools for hacking iPhones and Macs
ᗙ Scribble - beaconing system for Office documents
ᗙ Archimedes - a tool for performing MitM attacks
ᗙ AfterMidnight and Assassin - malware frameworks for Windows
ᗙ Athena - a malware framework co-developed with a US company
ᗙ Pandemic - a tool for replacing legitimate files with malware
ᗙ CherryBlossom - a tool for hacking SOHO WiFi routers
ᗙ Brutal Kangaroo - a tool for hacking air-gapped networks
ᗙ ELSA - malware for geo-tracking Windows users
ᗙ OutlawCountry - CIA tool for hacking Linux systems
ᗙ BothanSpy & Gyrfalcon - CIA malware for stealing SSH logins
ᗙ HighRise - Android app for intercepting & redirecting SMS data
ᗙ Achilles, Aeris, & SeaPea - tools for hacking Mac & POSIX systems
ᗙ Dumbo - tool to disable webcams and microphones
ᗙ CouchPotato - tool to capture remote video streams
ᗙ Angelfire - malware framework for hacking Windows PCs


Comments
Amigo-A - 6 years ago
CIA scare the whole world with Russian hackers, and they (CIA) go in closed doors without noise and dust and take what they want.
J_crowe - 6 years ago
Which one of the Vault7 tools should we all be worried about most?
Steve Holle - 6 years ago
Someone needs to hack WikiLeaks.