
Security experts have discovered a new strain of malware that targets vulnerable Linux-based systems and tries its best to avoid infecting devices on government and military networks.
The name of this new strain is GoScanSSH, and its name is a tell-tale sign of its main features and capabilities — coded in Go, use of infected hosts to scan for new ones, and the SSH port as the point of entry.
GoScanSSH is not your typical IoT bot
The infection process is a little bit complex, but this malware doesn't appear to be the work of an IoT botnet herder. Instead, this looks to have been created by an advanced threat actor that seems to be searching for footholds on internal networks, but being very careful to avoid infecting government, military, army, or law enforcement networks that may attract more scrutiny and possibly a legal investigation.
The process of a typical GoScanSSH infection is detailed below, and in more depth in a Cisco Talos report, here.
≫ The malware checks if the selected IP is on one of two IP blacklists (one with special-use addresses and one with IP ranges primarily controlled by various government and military entities)
≫ GoScanSSH scans the IP on port 22, looking for an open SSH port
≫ If the IP has an open SSH port, the malware runs a reverse DNS lookup to see if the IP hosts any websites/domains
≫ If the IP hosts a website, GoScanSSH runs the found domains against a second blacklist.
≫ This second scan checks if the domains have any of the following TLDs — .mil, .gov, .army, .airforce, .navy, .gov.uk, .mil.uk, .govt.uk, .mod.uk, .gov.au, .govt.nz, .mil.nz, .parliament.nz, .gov.il, .muni.il, .idf.il, .gov.za, .mil.za, .gob.es, .police.uk
≫ If the IP hosts any government, military, or law enforcement domain, GoScanSSH moves to a new IP address
≫ If the scanned IP is not on any of the two blacklists, the malware launches a dictionary brute-force attack in an attempt to guess the SSH credentials
≫ The malware uses a list of over 7,000 user-password combos
≫ Most combos are specific to Linux-based devices, while some combos are just the most common user-password combinations
≫ When the malware finds the remote device's SSH credentials, it reports back to its C&C server located on the Dark Web (communications occur via Tor2Web proxies)
≫ Crooks put together a unique version of the GoScanSSH malware binary
≫ They then log into the new devices manually and install this new GoScanSSH malware
≫ Malware runs a series of hash computations to determine the device's hardware capabilities and reports back to the C&C server
≫ GoScanSSh starts a scan for other devices to infect
Cisco Talos researchers say they've spotted over 70 unique samples of the GoScanSSH malware until now, and many of them had different version numbers (1.2.2, 1.2.4, 1.3.0, etc.). This suggests the malware's authors are still developing this new strain as they go.
Malware looks primed for mining, but more likely not
Some might suggest that the hash computations it runs on infected devices may suggest attackers may be inclined to installing a cryptocurrency miner on infected devices in the future. Researchers have not seen any such cases until today.
This theory might not be viable because of the list of default user-password combos the malware uses during the brute-force attack. According to Cisco experts, these credentials belong to IoT devices that are not equipped with the necessary hardware to handle cryptocurrency mining operations.
For example, during the brute-force attack, GoScanSSH uses the default creds associated with Open Embedded Linux Entertainment Center (OpenELEC) systems, Raspberry Pi boards, Open Source Media Center (OSMC) devices, Ubiquiti routers, PolyCom SIP phones, Huawei devices, and Asterisk servers.
GoScanSSH is a small botnet
For now, it is unclear what perpetrators are trying to achieve by deploying GoScanSSH, but by deploying the malware manually on each infected host and by carefully tiptoeing around government and military networks, this sure looks like someone trying to break into larger networks, potentially for orchestrating larger hacks.
This affinity for keeping a low profile is also evident because despite being active since June 2017, deploying 70 different versions and using over 250 distinct C&C servers, researchers found very few infected bots.
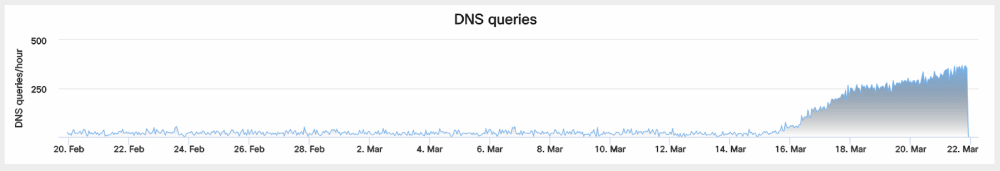
They were able to determine this by using passive DNS data for the domain names associated with the C&C servers. Researchers say they found a small number of requests for the C&C servers, suggesting this was a very small botnet.
According to Cisco's passive DNS data, the C&C domain with the largest number of DNS resolution requests had been seen 8,579 times, a very small number compared to most IoT botnets. Researchers probably wouldn't have spotted this new threat, if its activity didn't pick up tenfolds during the past ten days.


Comments
Highroller - 6 years ago
Rpi mediacenters would be a Great mining botnet, they are left alone idle for most of the day and they are often unatended so it wont be easily spotted that you are mining.