A new hacking campaign is underway that is targeting Chromecast adapters, Smart TVs, and Google Home in order to play a YouTube video promoting PewDiePie's channel.
Since the battle to have the most subscribers began between PewDiePie and T-Series, a hacker who goes by the name TheHackerGiraffe has been performing creative attacks that promote PewDiePie's channel.
First they started by sending print jobs promoting PewDiePie to Internet-connected printers and has now started to targeting Internet-connected devices that support Chromecast and forcing them to play the following YouTube video.
In this latest campaign, TheHackerGiraffe has teamed up with another hacker who goes by the name j3ws3r and borrowed the Chromecast attack code from FriendlyH4xx0r. This code utilizes APIs, such as the Google Home Local API, in order to connect to the device, rename it to "HACKED_SUB2PEWDS_[number]", and then play the above video on it.
TheHackerGiraffe told BleepingComputer that they were able to retrieve approximately 123,000 vulnerable devices using Shodan, with 100,000 being actually accessible. The hacking team also created a site at https://casthack.thehackergiraffe.com/ that provide real-time information on the attack and a running count of successfully attacked devices.
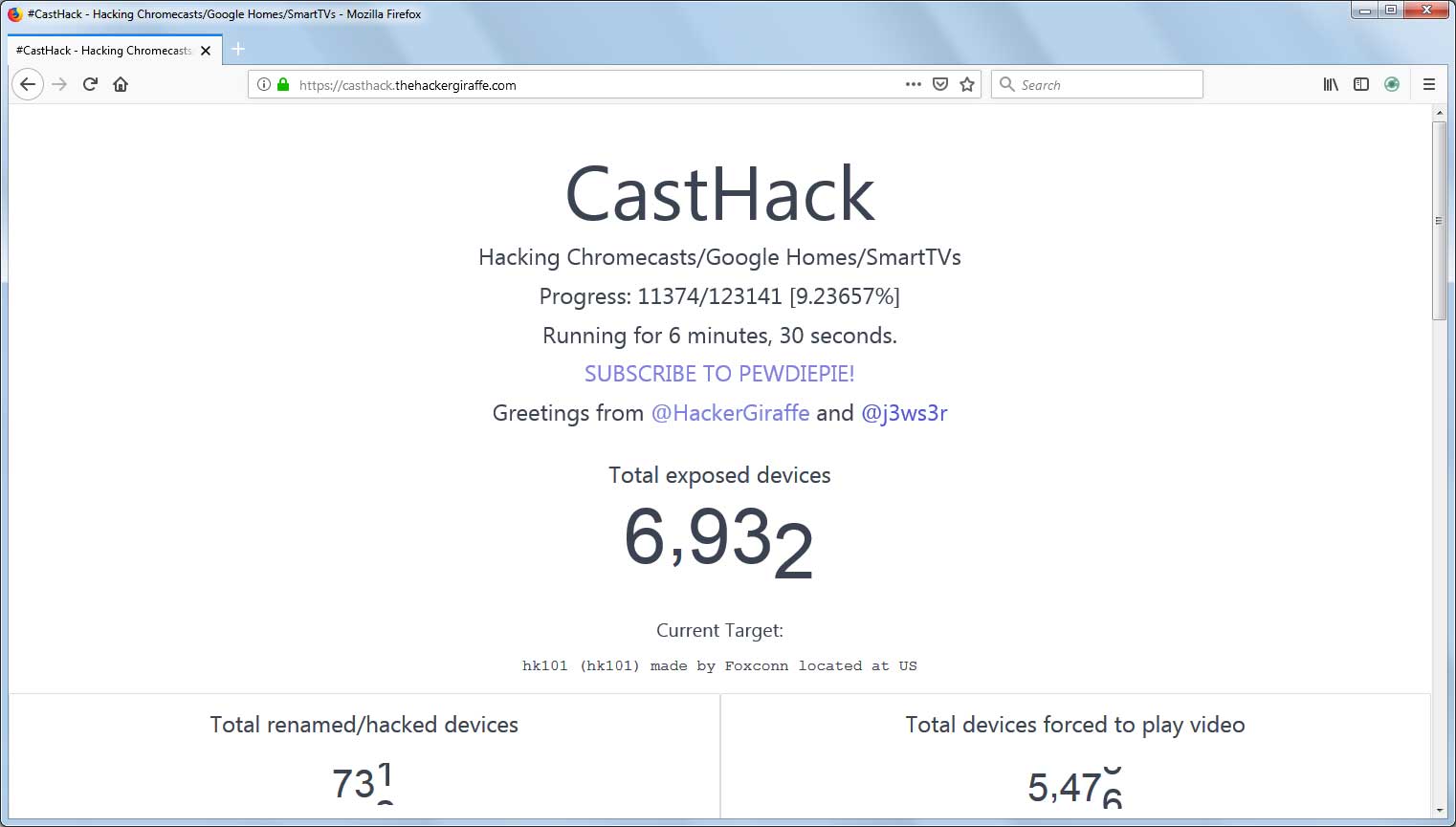
According to TheHackerGiraffe, when they first started the attack they were able to play the video on approximately 2,000 devices while targeting TCP ports 8008/8443, but soon after everything stopped working - even on their local devices. This has led the hacking team to think that Google had created an API hotfix that has prevented their attack from working.
"A few minutes after my attack started. I got around 2k devices before the endpoints stopped responding at all," the TheHackerGiraffe told BleepingComptuer via a private conversation. "The data harvesting endpoints still responded. And factory reset/reboots were still possible. Renaming also was still possible."
The team then switched to port 8009 in order to "use Google’s own cast protocol". So far, this appears to allow their attack to continue working.
While Google has not publicly stated that they have applied any hotfixes, a Chromecast engineer named Sarah Price has been active on Reddit asking for user's router information. It is possible that the collected information was used to put some sort of restriction in place to prevent the original attacks from working.
When asked why they are performing this attack, TheHackerGiraffe told us that they were doing it to raise awareness, gain experience, and have some fun.
"My motivation is to just raise awareness while having a bit of developer fun. I build scripts and websites. Get hands on experience with high traffic, but also raise awareness for this. This shouldn't be exposed at all"
Preventing Chromecast Attacks
The reason these attacks work at all is because the Chromecast devices are utilizing Universal Plug and Play (UPnP) to cause your Internet router to forward public Internet ports to the internal private Chromecast devices.
UPNP is used by local devices and your routers to make it easier for internal private network devices, like TVs, printers, and Chromecast devices, to be usable by remote devices. The problem is that it also exposes them to the Internet, which means attacks like the one described above can occur.
When BleepingComputer asked Google how to prevent these types of attacks, they responded that UPnP should be disabled on the user's router.
"To restrict the ability for external videos to be played on their devices, users can turn off Universal Plug and Play (UPnP). Please note that turning off UPnP may disable some devices (e.g. printers, game consoles, etc.) that depend on it for local device discovery."
TheHackerGiraffe has also told BleepingComputer that UPnP should be disabled and has been assisting those who email them to turn this "feature" off.
Below is a list of articles that detail how to turn off UPnP for various router manufacturers.
-
Netgear routers: https://kb.netgear.com/24306/How-do-I-enable-Universal-Plug-and-Play-on-my-Nighthawk-router
-
Linksys routers: https://www.linksys.com/nz/support-article?articleNum=135071
-
D-Link routers: https://eu.dlink.com/uk/en/support/faq/routers/wireless-routers/dkt-series/how-do-i-enable-upnp-on-my-dir-series-router
-
Verizon FIOS routers: Login to your router and go to this URL: http://192.168.1.1/index.cgi?active_page=900 (replace IP address with the IP address of your router)
-
TP-Link routers: https://www.tp-link.com/cz/faq-1669.html
-
Google WiFi: https://support.google.com/wifi/answer/6274337?hl=en
-
Eero routers: https://support.eero.com/hc/en-us/articles/207613326-What-advanced-features-does-eero-support
If you have any other articles for other manufacturers, feel free to leave them in the comments and we will get them added.


Comments
buddy215 - 5 years ago
ROKU devices do not need UPnP.....no need for Chromecast if you have one of those.