
The Conti cybercrime syndicate runs one of the most aggressive ransomware operations and has grown highly organized, to the point that affiliates were able to hack more than 40 companies in a little over a month.
Security researchers codenamed the hacking campaign ARMattack and described it as being one of the group’s “most productive” and “extremely effective.”
Lightning-fast ARMattack campaign
In a report shared with BleepingComputer, researchers at cybersecurity company Group-IB say that one of Conti’s “most productive campaigns” occurred last year, between November 17 and December 20, 2021.
They discovered the group’s month-long hacking spree during incident response activities and dubbed it ARMattack, based on a domain name that exposed the gang’s infrastructure.
During the campaign, Conti affiliates managed to compromise more than 40 organizations in various sectors of activity operating across wide geography but with a focus on companies based in the U.S.
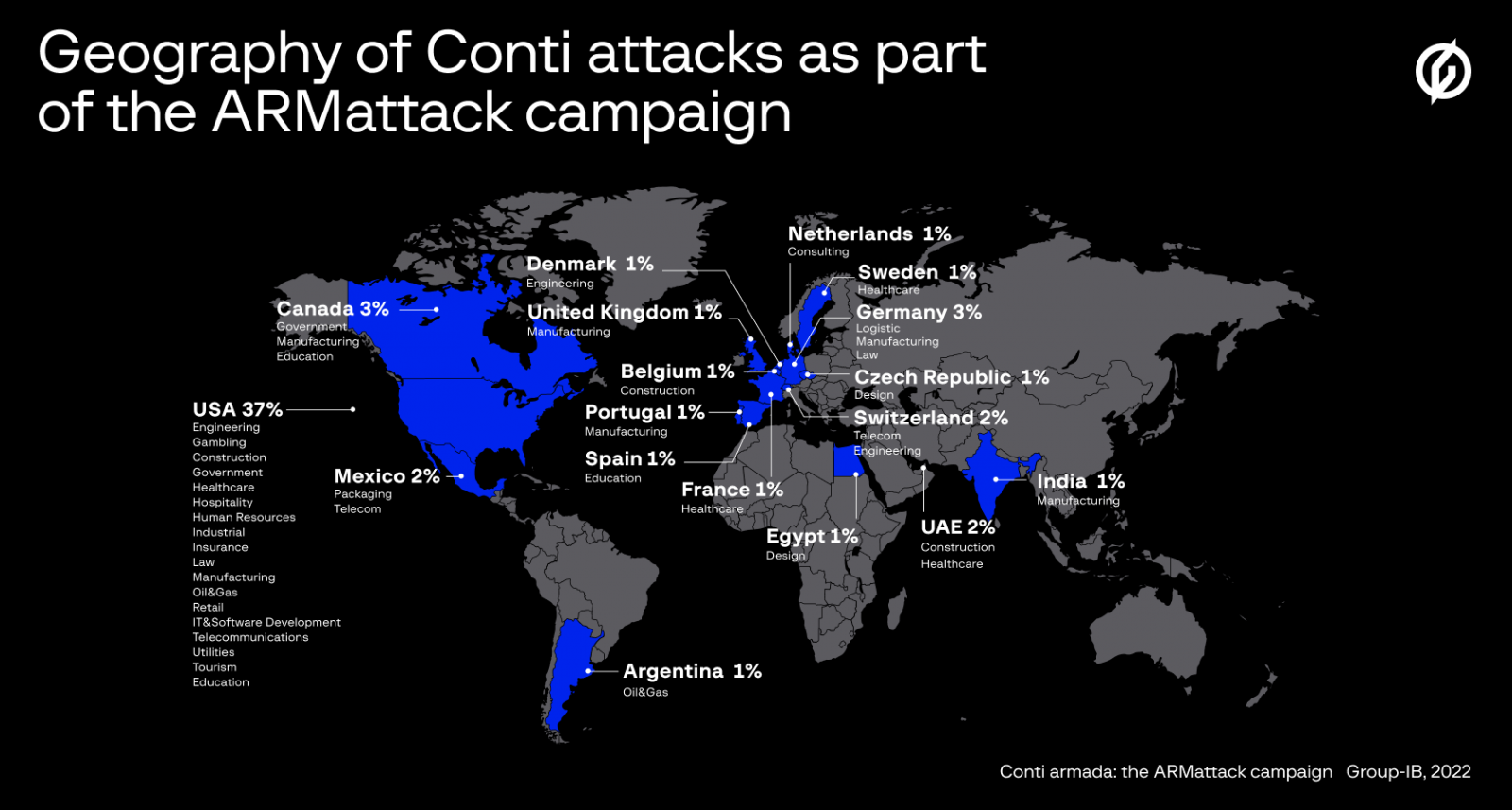
A Group-IB spokesperson told BleepingComputer that ARMattack was very swift and explained that the company’s report refers to organizations that had their networks compromised. It is unknown whether any of the victims paid the ransom demanded by the attacker.
It is worth noting that while the Conti leak site published data for as many as 46 victims in just one month (e.g. April 2022), the compromise date remains unclear.
Based on data from Group-IB, Conti’s shortest successful attack lasted for just three days from initial access time to encrypting the organization’s systems.
“After gaining access to a company’s infrastructure, the threat actors exfiltrate specific documents (most often to determine what organization they are dealing with) and look for files containing passwords (both plaintext and encrypted). Lastly, after acquiring all the necessary privileges and gaining access to all the devices they are interested in, the hackers deploy ransomware to all the devices and run it” - Group-IB
“Office” hours
Using data gathered from public sources, such as the leaked internal chats from the gang, Group-IB has been analyzing Conti’s “working hours.”
According to the researchers, Conti members are active about 14 hours every day, except during the New Year holiday, a schedule that accounts for their efficiency.
Group-IB says that the group starts working towards noon (GMT+3, Moscow time) and retreats after 9 PM. Conti members are likely dispersed across multiple time zones.
Furthermore, the researchers highlight that the group functions similarly to a legitimate business, with individuals tasked with finding workers, research and development, running OSINT jobs, and providing customer support.
Conti’s efforts to stay ahead of the game include monitoring Windows updates and analyzing the changes from new patches, as well as discovering zero-day vulnerabilities that can be used in attacks, and exploiting freshly disclosed security flaws.
“Conti’s increased activity and the data leak suggest that ransomware is no longer a game between average malware developers, but an illicit RaaS industry that gives jobs to thousands of cybercriminals worldwide with various specializations” - Ivan Pisarev, Head of Dynamic Malware Analysis Team at Group-IB’s Threat Intelligence team
At the top of the ransomware game
Conti is currently one of the top three ransomware gangs in terms of attack frequency, falling second after LockBit this year, as per data collected from the first quarter of 2022.
Since the gang came into the public light, the list of victims attacked with Conti ransomware that did not pay the threat actor increased to 859, although the real number is likely significantly higher since the count is only based on data published on the group’s leak site.
Judging by this number alone, on average, Conti has been publishing each month data stolen from at least 35 organizations that did not pay a ransom.
The first Conti ransomware attacks that BleepingComputer learned of date from late December 2019. According to Group-IB, initial test versions of the malware have been tracked to November 2019.
One of the most notorious Conti attacks occurred recently, encrypting systems from multiple government bodies in Costa Rica, causing the country’s president to declare a national state of emergency.
Despite the recent chat and source code leaks, Conti continues to run a lucrative business that has shown little sign of collapsing.
The group has constantly expanded its activity by working with other ransomware operators (HelloKitty, AvosLocker, Hive, BlackCat, BlackByte, LockBit) and acquiring cybercriminal operations such as TrickBot.
Despite these moves to expand their business, the Conti team leaders announced in May that the brand no longer existed and took their backend infrastructure offline.
While the payment and data leak sites were still operational, researchers state that this was being done to make it appear as if they were still operating as normal.
However, the syndicate continued to live, with Conti leadership partnering with smaller ransomware gangs for attacks, in an effort to splinter into smaller cells instead of rebranding into a larger operation.
This would result in experienced cybercriminals spreading to other ransomware businesses while still being loyal to the Conti syndicate.
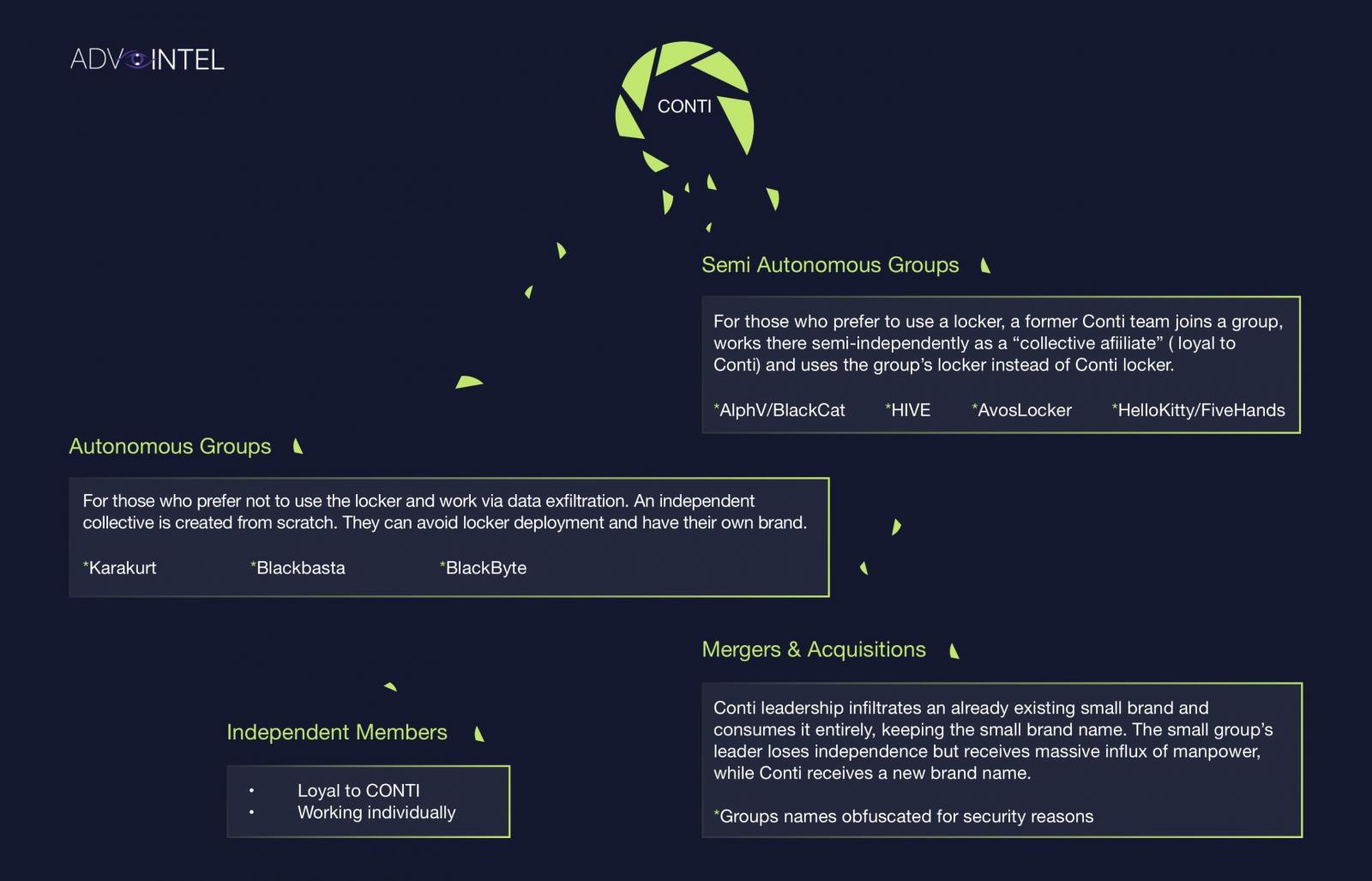
Conti has become a threat so large that the U.S. Government is offering a reward of up to $15 million for information leading to the identification and location of the group’s leading members.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now