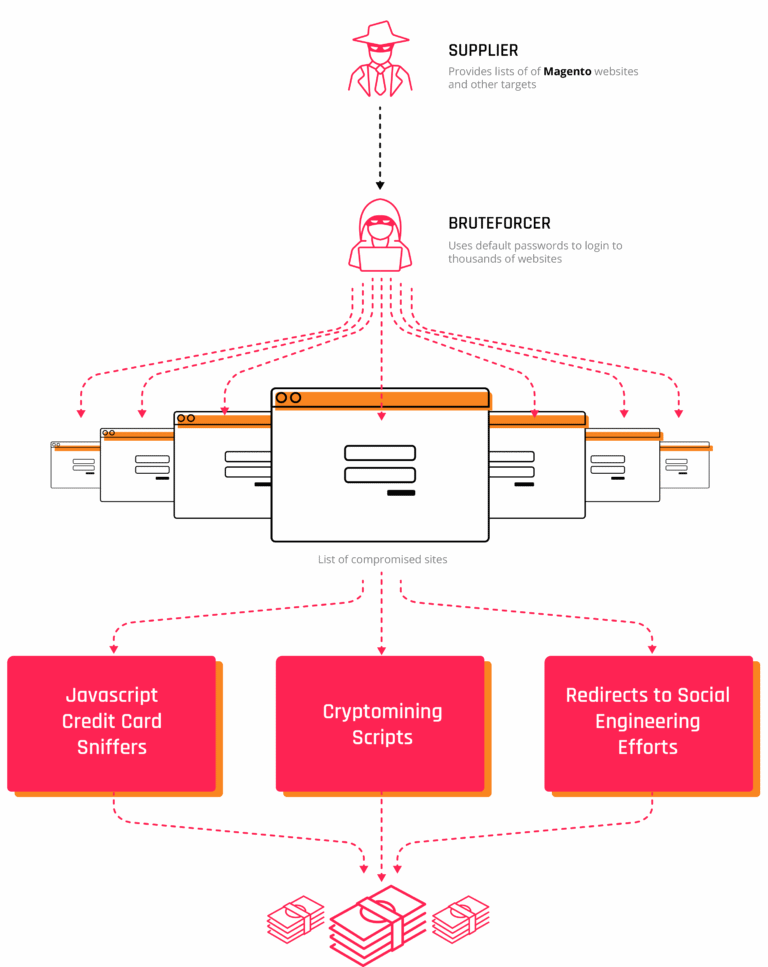
Security researchers say they've identified at last 1,000 Magento sites that have been hacked by cybercriminals and infected with malicious scripts that steal payment card details or are used as staging points in the delivery of other malware.
"The Magento sites are being compromised through brute-force attacks using common and known default Magento credentials," Flashpoint researchers say.
"Brute-force attacks such as these are simplified when admins fail to change the credentials upon installation of the platform," researchers add. "Attackers, meanwhile, can build simple automated scripts loaded with known credentials to facilitate access of the panels."
Hacked sites used for cryptojacking, card scraping, more
Once attackers gain access to these sites, researchers say they've observed three main patterns of malicious activities.
The most common practice is to insert malicious code in Magento core files, code that logs payment card information entered inside the checkout process. Such malware is named a card scraper, and users should expect to find one on any e-commerce store that looks to have missed a few updates.
Second, attackers also deploy cryptojacking scripts that mine Monero on the computers of store visitors, a practice that has become quite common these days, across all sites, not just Magento stores.
Last but not least, hackers also use these compromised Magento stores to redirect some of the infected sites' visitors to malicious sites that attempt to trick users into downloading and installing malware on their computers. According to cases investigated by Flashpoint researchers, the most prevalent tactic was to redirect users to sites offering phony Adobe Flash Player update packages, which would infect users with the AZORult infostealers.
According to researchers, the vast majority of these 1,000+ compromised sites were in the education and healthcare sectors, with the vast majority of compromised sites hosted on servers located in UE and the US.
More hacked Magento sites are still out there
Security experts believe that the sites they discovered are only a small sample of all the compromised Magento stores.
Flashpoint says that besides Magento, threat intelligence gathered from entry-level and top-tier Deep & Dark Web forums suggests that cybercriminals are also very interested in other e-commerce platforms, not just Magento, such as OpenCart and Powerfront CMS.
In today's cybercrime landscape where criminals have access to cheap brute-forcing botnets that they can use to guess site passwords with relatively little effort, site owners should make sure they use unique usernames and passwords that can't be guessed after a few attempts.
Securing admin account passwords should be a top priority —next to applying security updates— for all site owners, not just those managing online stores.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now