
A United Arab Emirates based cybersecurity company named DarkMatter wants to become a trusted root certificate authority in Firefox and security professionals around the world are concerned.
When a browser or operating system trusts a root certificate authority, it means that any SSL certificates issued by that CA will also be considered valid. For this reason, only those root CAs that have been properly vetted, follow Mozilla policies, and have not shown any reason for concern should be added as a trusted root CA.
While DarkMatter is currently not a trusted root CA in Firefox, their certs are automatically considered valid because they are cross-signed through a trusted root CA named QuoVadis. This is shown below in the SSL certificate for darkmatter.ae, which shows Quovadis Root CA2 G3, which is owned by DigiCert, as the root certificate.
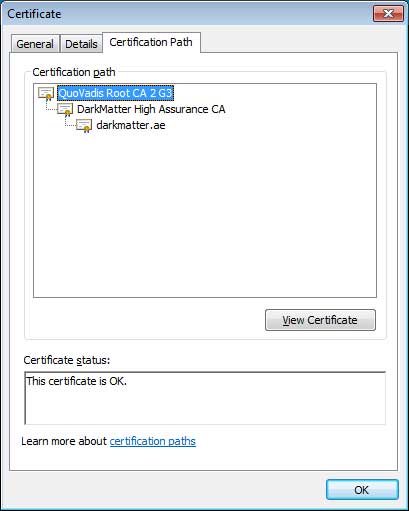
In a Mozilla Bugzilla request, Scott Rae, Senior Vice President for Public Key Infrastructure at DarkMatter, is requesting that DarkMatter be accepted as a trusted root CA in Firefox. This would allow any certificates that they issue to automatically be trusted in Firefox without having to be cross-signed by QuoVadis.
In their request, the security company explains that the UAE Global Root CAs are currently operated under a joint stewardship between DarkMatter and the UAE government. As they are one of the caretakers for the UAE National PKI, it would make sense for them to be a trusted root authority in their own right.
"As the UAE transitions from a petrochemical dominated economy to an information and finance driven economy, the desire to have a security infrastructure to underpin and support this is critical to its success. DarkMatter has been trusted with the task of setting up and operating the UAE National PKI as a result. DarkMatter also provides a full range of cyber security services to other governments, private enterprises and public organization on a global basis. To the extent that the UAE residents or global DarkMatter customers utilize Mozilla products, embedding of the UAE and DM Roots will facilitate seamless trust and cyber security services for these entities. DM Trust Services (the name typically grouping PKI and Identity services from DarkMatter), are utilized to secure web sites, web services, and TLS based communications. They are also utilized for securing email, document signing, and facilitating strong authentication for DM customers."
DarkMatter has also promised to publish "ALL of its publicly trusted TLS certs to Certificate Transparency logs." Certificate Transparency is a framework that allows for the monitoring of new certificates as they are created in order to find ones that are invalid of malicious in nature.
From their request and promises, adding them as a root CA seems logical and one that would not normally be questioned by Mozilla or other trusted root authority maintainers. Recent reports, though, stating that DarkMatter is tied to government-sponsored hacking groups are causing hesitation and debate among security professionals.
Security and privacy professionals are concerned
When it comes to trusted root certificate authorities, "trust" is the most important word. This is because root authorities are not only expected, but trusted, to vet all certificate requests and to not issue certificate for domains to those who do not have the right to them.
If a root authority wrongly issues a SSL certificate for a domain, it could allow attackers to masquerade as a legitimate site or perform man-in-the-middle attacks (MiTM) to steal credentials, data, and listen in on normally encrypted traffic using the wrongfully issued cert. Trusted root CAs in Windows could also misissue code-signing certificates that could allow attackers to spread malware that appears to be signed by well-known companies.
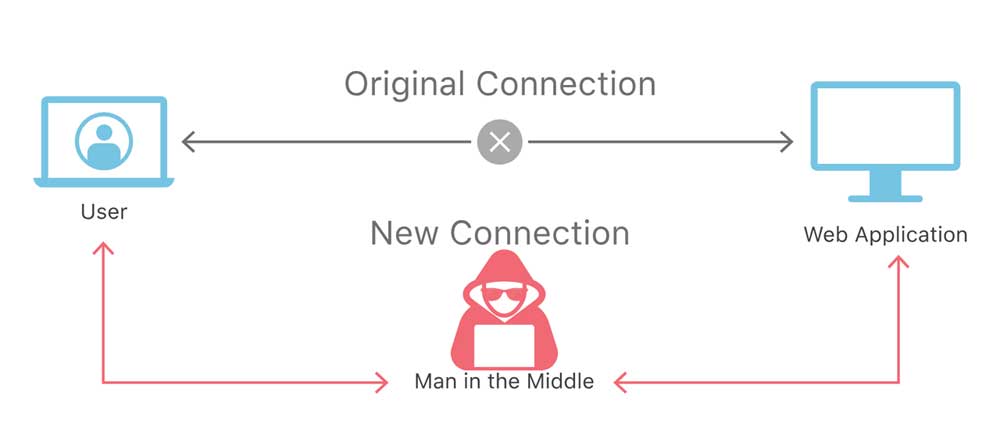
When it comes to DarkMatter, there is a lack of trust due to a recent Reuters article that states that the cybersecurity company is allegedly tied to a hacking group called Project Raven who works for the United Arab Emirates. This hacking group reportedly includes "more than a dozen former U.S. intelligence operatives recruited to help the United Arab Emirates engage in surveillance of other governments, militants and human rights activists critical of the monarchy."
While DarkMatter denies that their CA will be used for anything other than legitimate certificate issuance, security professionals are concerned that they may not be telling the truth.
Over the past week, BleepingComputer has been speaking to numerous security researchers and developers of the most popular web browsers, and while most have not wished to be cited due to corporate conflicts, almost all of them have had concerns about DarkMatter certificates being trusted.
As part of this story, we spoke to Jonathan Rudenberg, one of the most active participants in the Mozilla.dev.security.policy mailing list and is known for detecting CA misbehaviors.
When asked about concerns that adding DarkMatter as a trusted root CA would put them in a good position to perform cyberattacks, Rudenberg acknowledged that this is a valid concern not only for DarkMatter, but for all CAs.
"Yes, all CAs in a root store are technically capable of issuing certificates that could be used for attacks that impersonate any website which is why it's so important that only competent and trustworthy organizations are trusted to act as CAs. All trusted CAs are expected to validate all information in certificates that they issue. If a CA issues a certificate with unvalidated information to a malicious party, it would enable attacks that intercept and modify information. For example, if a CA issued a certificate for a bank's website to a malicious party, it would allow whoever held the certificate and private key to intercept passwords and tamper with the information that end-users see when visiting the website."
While Certificate Transparency Logs should make it easier to spot bad behavior, Andrew Ayer, the owner and creator of SSLMate's Certspotter, has stated that this could be bypassed to hide misissued certificates.
"I would also note that while DarkMatter has promised to log all certificates they issue to public Certificate Transparency logs, which anyone can look through for suspicious certificates, this doesn't provide any assurance. This is because Firefox does not currently enforce Certificate Transparency, meaning DarkMatter could simply choose not to log the certificates they use for MitM. Apple and Chrome have begun enforcing Certificate Transparency for new certificates, but this could be bypassed if DarkMatter backdated their MitM certificates."
Furthermore, Rudenberg explained that many applications utilize Mozilla's root store and if DarkMatter is added as a trusted root CA, then those applications would automatically trust their certificates as well. This includes programs such as Chrome on Linux, Thunderbird, and more.
'The Mozilla root store is used both by the Firefox browser and many other projects that are not affiliated with Mozilla, as it is the only root program that is completely managed in public and invites community discussion about decisions. Most Linux distributions, many programming languages and libraries, and many products developed by other companies use derivatives of the Mozilla root store. So CAs that the Mozilla root store trusts impact users across the world whether or not they use Firefox."
Ultimately, the same concerns that researchers have with DarkMatter could be said for any CA. The difference, though, is that DarkMatter has a reportedly tarnished history that trusted store maintainers are having trouble ignoring.
Discussions turn to distrusting all DarkMatter certs
While previously the discussion was about whether DarkMatter should be allowed to become a trusted root certificate in Firefox, it has now turned to whether DarkMatter's intermediate certificates with QuoVadis should also be distrusted.

In a conversation titled "DarkMatter Concerns" posted to the mozilla.dev.security.policy mailing list over the weekend, Mozilla's Certificate Authority Program Manager Wayne Thayer has asked whether they should not only deny the pending trusted root authority request, but also distrust their intermediate CA certificates signed by Quovadis.
"The purpose of this discussion is to determine if Mozilla should distrust DarkMatter by adding their intermediate CA certificates that were signed by QuoVadis to OneCRL, and in turn deny the pending root inclusion request."
Thayer goes on to say that while DarkMatter has not shown any signs of misissuance, Mozilla's policy allows them to use their discretion on how to better protect users of their root store.
"Mozilla’s Root Store Policy [8] grants us the discretion to take actions based on the risk to people who use our products. Despite the lack of direct evidence of misissuance by DarkMatter, this may be a time when we should use our discretion to act in the interest of individuals who rely on our root store."
Cooper Quintin of the EFF also posted his concerns along with a link to a recent article that he wrote regarding DarkMatter's request. Other comments come from Debian's OpenSSL maintainer Kurt Roeckx, Amnesty International's Claudio Guarnieri, and Jonathan Rudenberg.
In reply to these concerns, DarkMatter's Rae stated that they are solely focused on defensive cyber security and have never performed attacks against any nationality. When Guarnieri pointedly asked Rae if he was denying the accuracy of the reports from Reuters and others, Rae never responded to him.

This discussion is still active and while some comments state that DarkMatter should not be punished for some perceived future threat, many others feel that the recent reports are a risk that should not be ignored.
BleepingComputer has reached out to Google and DarkMatter with questions related to this story, but had not heard back by the time of this publication.
Update 2/25/19: DarkMatter's CEO Karim Sabbagh has attached a reply to Mozilla bug ticket regarding the concerns about adding them as a trusted root CA. While the letter states that DarkMatter is "soley focused on defensive cyber security", it also states that they won't "comment on the practices of government entities and other companies mentioned in a media report".
In response, Ryan Sleevi, a software engineer at Google, added his concerns to the mozilla.dev.security.policy regarding how to proceed with vetting root CAs and sub-CAs in the future.
Distrusting DarkMatter's certificates
If you are concerned about your operating system or browser automatically trusting DarkMatter's certificates, you can distrust them by removing QuoVadis' certificates from the trusted root certificate authorities in Windows and your browsers.
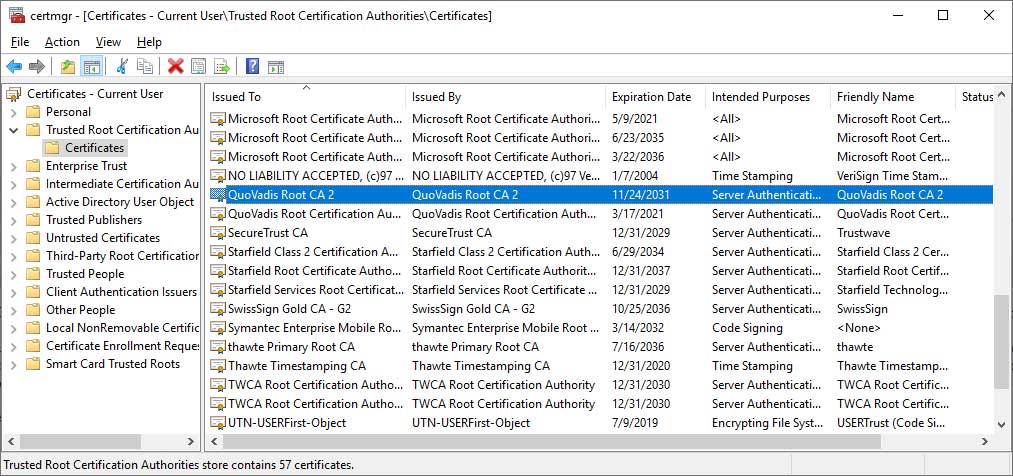
This is not advised as QuoVadis is a legitimate CA and removing them will cause any certificates that they have issued to become invalid.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now