Security researchers report a massive uptick in the number of MongoDB databases hijacked and held for ransom. On Monday, researcher Niall Merrigan reported 28,000 misconfigured MongoDB were attacked by more than a dozen hacker groups. That’s sharp increase from last week when 2,000 MongoDB had been hijacked by two or three criminals.
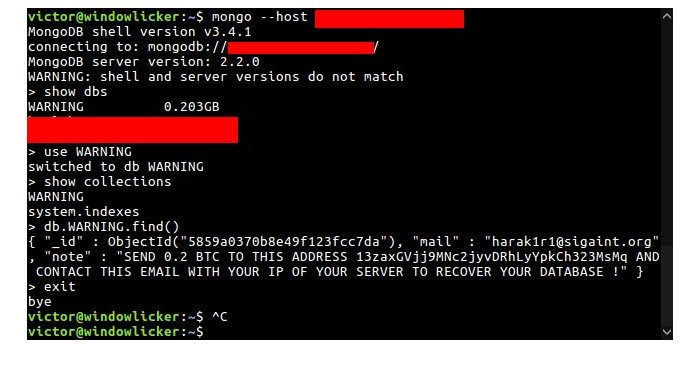
A wave attacks was first spotted on Dec. 27 by Victor Gevers, an ethical hacker and founder of GDI Foundation. That’s when he said a hacker going by the handle “Harak1r1” was compromising open MongoDB installations, deleting their contents, and leaving behind a ransom note demanding 0.2 BTC (about $220).
Victims would discover they were hit with the data theft only when they accessed the MongoDB and came across a top database field with the ransom demand that read, “Contact this email with your IP of your server to recover your database.”
Escalation of the attacks happened fast jumping from 200 14 days ago to 2,000 the following week. On Friday the numbers were at 10,000, and by Monday Merrigan said there was a huge spike in attacks via his Twitter account reporting 27,000 servers compromised representing 93 terabytes of data gone.
WHOA… Latest #mongodb download from @shodanhq massive jump in ransomed databases 93TB gone (snapshots taken at 1530 and 2130 CET) pic.twitter.com/MakOlrbptt
— Niall Merrigan (@nmerrigan) January 8, 2017
Merrigan and Gevers have been tracking both the number of attacks and the number of groups behind them via a spreadsheet with the latest updates. As of this writing, close to 28,332 victims have been reported.
Since identifying “Harak1r1” as the original attacker, they say more than a dozen additional hackers are now actively targeting MongoDB installations as well. Researchers said that in many cases, data stored in the MongoDB now is simply being destroyed and when victims pay the ransom they do not receive their data back.
Last week, Gevers told Threatpost attackers were battling among themselves. He said, when one hacker would leave a ransom note, another hacker would target the same database, delete the original ransom note and leave their own. This further complicates a victim’s ability to retrieve data even if a ransom is paid, he said.
The problem stems from companies that have used the default installation configuration for MongoDB, which does not require authentication to access the database. Researchers say hackers using a Shodan query or scanning the Internet for vulnerable installations can easily find MongoDB servers online.
Gevers said a recent scan using Shodan revealed 46,000 open MongoDB ripe for attack. He added that an uptick in victims is due to the fact attackers have automated attacks via scripts. He added that because the MongoDB configurations require no credentials, the script used in the attacks is simple to write and execute.
Representatives at MongoDB did not return calls for comment. However, last week when initial reports of MongoDB databases being compromised began to surface, the company published instructions on how admins can secure their databases and respond to attacks.